Nightfall Sensitive Data Protection for Email
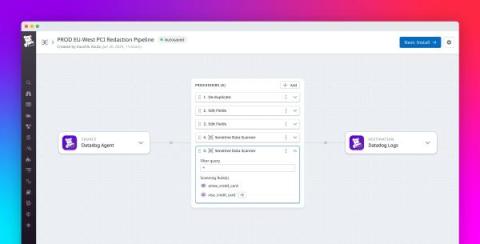
Leverage Nightfall’s AI-native platform to pinpoint and protect PII, PCI, PHI, secrets, and credentials across SaaS and email, including Gmail. Built with AI at the core, Nightfall Sensitive Data Protection is transforming email DLP by helping security teams to… … detect sensitive data with 2x better precision and 4x fewer false positive alerts. … act swiftly by blocking or quarantining emails, or removing attachments that contain sensitive data.