Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Data Security
The latest News and Information on Data Security including privacy, protection, and encryption.
The never-ending story: Microsoft AI team accidentally exposed 38 Terabytes of internal data
The accidental sharing of cloud access is an all-too-familiar story. In one latest incident, Microsoft’s AI research team accidentally exposed to the public 38 Terabytes of private data including internal messages, private keys, and passwords, according to a recent report . And all it took to cause this gigantic exposure was a few errant clicks in a configuration menu.
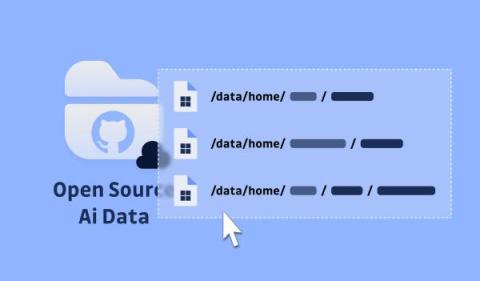
Microsoft AI involuntarily exposed a secret giving access to 38TB of confidential data for 3 years
Discover how an overprovisioned SAS token exposed a massive 38TB trove of private data on GitHub for nearly three years. Learn about the misconfiguration, security risks, and mitigation strategies to protect your sensitive assets.
What Are Data Leaks?
Data leaks occur when sensitive data is unintentionally exposed from within an organization. Data leaks can refer to both the leakage of digital data, meaning anything that can be transmitted through the internet, as well as physical data, such as USB drives. Continue reading to learn how data leaks happen, how serious they can be and how to prevent them from occurring.
archTIS wins the 2023 Australian Defence Industry Award for Cyber Business of the Year two years in a row
Friends and Colleagues, We are proud to share that archTIS has won the 2023 Australian Defence Industry Award for Cyber Business of the Year for the second year running. We are humbled to once again be recognised by our peers and industry leaders for the valuable contributions and leadership role archTIS has taken in solving the critical Defence challenge of securing sensitive and classified information sharing.
The Best And Easiest Ways To Secure The Data In Your Company
A Comprehensive Guide to Securing Data in the Digital Age
In today's rapidly evolving digital landscape, data stands as the linchpin of modern business operations. However, safeguarding sensitive data has grown into a formidable challenge for enterprises in recent times. The surge in data volume and escalating threats are not the sole culprits; the pivotal shift toward digitalization has prompted organizations to migrate their data and IT infrastructure to a diverse blend of private and public clouds.
Collaboration: The Key Ingredient to Successful Security Compliance
In the fast-paced world of software development, the clash between developers and security experts could greatly benefit from some much-needed balance. On one side, developers strive for success based on metrics like delivery time, deployment frequency, and number of features. On the other side, security professionals are measured on vulnerability and compliance metrics.
Bridging the gap between data security and privacy
Introducing Data-centric Policy-enforced Access Control and Data Protection for NetApp ONTAP
As increased cyber threats and regulations governing the handling of sensitive personal data, government and defense data are enacted, the ability to automate the discovery, classification and protection of sensitive information is critical across enterprise content management systems. To this end, archTIS recently extended NC Protect’s capabilities to support NetApp ONTAP to ensure we support a wide range of enterprise platforms.