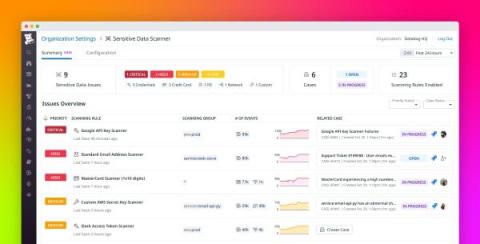
Discover, triage, and remediate sensitive data issues at scale with Sensitive Data Scanner
Managing sensitive information in your telemetry data poses many challenges to governance, risk management, and compliance (GRC) teams and overall security. Organizations in healthcare, finance, insurance, and other fields must carefully adhere to strict compliance requirements. But sensitive data comes in many forms and moves between many endpoints, and as a result, it can easily become exposed in telemetry data.