Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2023
What is Continuous Auditing?
How to Prioritize Risks in the External Attack Surface Effectively
What Is Practitioner-Focused Cybersecurity?
A basic Google search for the term “cybersecurity” will turn up dozens of competing advertisements for companies promising to solve all your security woes and keep attackers at bay with their version of a “technology silver bullet” – the end all be all that you must, according to them, purchase right now. It’s not that technology isn’t essential to your security strategy; it’s vital!
Privacy Risk Management Across the Data Lifecycle
What is the FFIEC Cybersecurity Assessment Tool?
The FFIEC Cybersecurity Assessment Tool (CAT) is a diagnostic test designed to help institutions identify risks and gauge cybersecurity preparedness. The tool is primarily for financial and non-depository institutions, enabling organizations to make risk-driven security decisions informed by regular cybersecurity assessments and standardized risk measurement criteria.
Android Malware Outbreak: Unmasking the RAT Inside a Screen Recording App
With the worldwide popularity of Android and its open-source software, hackers have an increased incentive and opportunity to orchestrate attacks. A Google search for “Android malware” brings up headlines like these, all from the past few days or weeks: SecurityScorecard recently analyzed a specific threat known as the AhMyth RAT (remote access trojan), which made headlines for infiltrating a popular screen recording app on the Google Play Store.
5 Essential Elements of a Municipal Cyber Security Plan
What is the Mitre ATT&CK Framework?
In cybersecurity, being well-versed in the wide range of resources available for protecting and enhancing your digital environment is crucial. One of the most significant and effective tools is the Mitre ATT&CK Framework. Read on for an in-depth exploration of this critical cybersecurity framework and how you can apply it to your own organization.
SecurityScorecard and the U.S. Chamber of Commerce
This week, SecurityScorecard is participating in the US Chamber of Commerce’s Cyber Security Trade Mission to Israel. This has been a valuable experience to not only share our cybersecurity knowledge, but to learn more about Israel’s cybersecurity efforts, and those of other countries.
Obrela at CRESTCon Europe | Interview Iraklis Mathiopoulos, Chief Services Delivery Officer
Increase Cyber Resilience With the Trusted, Must Have Standard for Measuring Cyber Risk
6 Benefits of Internal Auditing
7 Keys to Perfecting Your Cyber Risk Management Strategy
How SMBs Can Build an Effective Risk Management Plan
SecurityScorecard's Cyber Resilience Services
With the average cost of a data breach now at $4.35 million, organizations need to take proactive measures to protect themselves and their data against cyber threats. Having a plan in place for how to respond to cyber incidents is an important step in increasing cyber resilience, protecting sensitive data, and saving money. But where should an organization start? And who should it trust?
Fighting Together: TSA, Critical Infrastructure, and Cyber Risk Management
Following the ransomware attack on a US pipeline company in May of 2021, the Transportation Security Administration (TSA) issued a series of security directives to enhance the cybersecurity posture of US transportation systems to mitigate cyber threats.
Free NIST CSF Vendor Questionnaire Template
Fortinet Fortigate Vulnerability CVE-2023-27997: How to Surface Exposed Devices and Mitigate the Threat
Recently, a critical vulnerability tracked as CVE-2023-27997 was identified in Fortinet Fortigate appliances. Fortinet makes some of the most popular firewall and VPN devices on the market, which makes them an attractive target for threat actors. This vulnerability has been exploited by the Chinese APT group Volt Typhoon, among others, targeting governments and organizations worldwide. As a result, Fortinet has released an urgent patch for affected systems.
Cybersecurity KPIs to Track + Examples
Cybersecurity Risk is a Business Risk: Upcoming SEC Regulations Make Security Transparency Mandatory
The upcoming cybersecurity regulations from the U.S. Securities and Exchange Commission (SEC) deliver a clear message: Cyber risk is a business risk. Slated to be finalized this fall, the regulations will directly link financial performance to cybersecurity through required public disclosures. If a company is hacked, it can affect the stock price, the market capitalization, and customer trust. That is why the SEC is paying attention and has proposed these vital regulations.
The key to 21 CFR Part 11 Compliance
21 CFR Part 11 is a set of regulations issued by the U.S. Food and Drug Administration (FDA) that establishes the criteria under which electronic records and signatures are considered trustworthy, reliable, and equivalent to paper records. In order to sell products in the United States, companies must demonstrate that their systems meet the standards set forth in Part 11. This can be a daunting task, as the requirements are numerous and detailed.
New CISA Directive Highlights Vulnerabilities at Network Edge
After a wave of zero-day attacks targeting widely used security and networking appliances, the Cybersecurity & Infrastructure Security Agency (CISA) is taking new measures to protect Internet-exposed networking equipment.
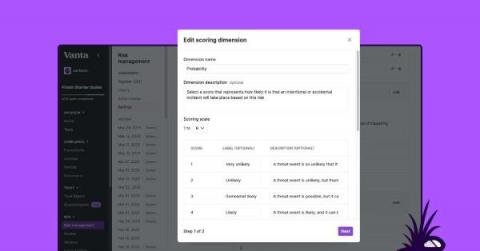
Improve your risk posture: Introducing Risk Management customization
Today we’re excited to announce Risk Management customization, a collection of new capabilities in our platform that enhance the existing Risk Management solution and give you more flexibility to enable custom risk management scoring and prioritization. Currently in beta, Risk Management customization will be generally available in the coming months.
Managing Cyber Risk in the Insurance Supply Chain
This week in London, SecurityScorecard hosted a roundtable discussion on cyber risk in the insurance supply chain. Keynote speaker Santosh Pandit, head of Cybersecurity at the Bank of England, shared his insights with 20 London-based insurers on managing cyber risk in the financial sector and the latest regulatory initiatives that may impact the insurance industry.
SecurityScorecard Identifies Infrastructure Linked to Widespread MOVEit Vulnerability Exploitation
New disclosures regarding the widespread exploitation of CVE-2023-34362, a new vulnerability affecting the MOVEit file transfer software, and the Cl0p ransomware group’s claim of responsibility for its widespread exploitation and the resulting data theft, have continued in the weeks since the vulnerability’s original publication.
3 Steps to Bridge Cyber Risk Communication Gaps
How to Create a Vendor Risk Management Checklist
Verizon 2023 DBIR: The Missing Pieces you Need to Take Action
Evidence-Based Strategies to Lower Your Risk of Becoming a Ransomware Victim
Debunking the Misconception That CRQ Requires a Lot of Data Collection
A Guide to Handling the MOVEit Attack
Last week, a vulnerability in the popular MOVEit managed file transfer service was exploited by the CL0P ransomware gang to execute data breaches – an increasingly common cybersecurity attack technique where popular software is exploited to target, by extension, their users. Victims of this hack include British Airways, Boots, BBC, and multiple US government agencies.
The CyberShield Event | Safeguarding The Digital Landscape
5 Effective Strategies to Mitigate Market Risk
Cybersecurity Risk Assessment Tools You Can Use Year-Round
Mend.io Launches AppSec Risk Assessment Program
At Mend.io, we’re always looking for ways to help organizations understand their application security risk. This week, we’re proud to announce a new initiative designed to make it easier than ever for organizations to visualize and remediate their biggest sources of risk: the Mend.io AppSec Risk Assessment Program.
5 Cyber Threat Prevention Strategies to Protect Your Growing Digital Footprint
GPT-4 Natural Language Global Search
How do subdomain takeovers work?
Data Privacy Lessons from Meta's $1.3 Billion GDPR Fine (& James Bond)
How to Choose a Compliance Management Tool
IT Audit Checklist for Your IT Department
Risk Registers: The Ultimate Guide with Examples & Template
Effectively utilizing a risk register allows your organization to anticipate and overcome challenges with confidence. No GRC program is failproof, which is why it’s so critical to take a thorough look at potential risks and remediations. To make sure you’re starting on the right foot, we’ve provided a free, downloadable risk register template you can use once you have a better understanding of what it does.
Software quality: Diligence prep for sellers
MOVEit File Transfer Zero-day Compromises Multiple Organizations
Product Spotlight Q2 2023
UpGuard Summit May 2023 - Panel Discussion
Forbes Media Publishes Industry's First List of America's Most Cybersecure Companies
In a climate where companies largely gain attention only when something negative happens, it’s time to celebrate and recognize the companies who are best in class when it comes to cybersecurity. That’s why we applaud Forbes’ decision to produce the industry’s first list of America’s Most Cybersecure Companies. These companies illuminate how cybersecurity is being taken seriously as a core business issue.
Protect your organization and vendors from subdomain takeovers
Leverage UpGuard's robust reporting functionality
Time savers to help optimize your Vendor Risk Management
ChatGPT and Software Supply Chain Risks
While some of the obvious misuse of ChatGPT in the world of cyber security was not unexpected – asking the artificial intelligence to write harder-to-detect malware and easier-to-convince phishing emails – a new threat has emerged that can leverage the very nature of the large language model. Ultimately, ChatGPT is a learning machine, and bases its answers on information it sources from the Internet.
Three Steps to Prevent a Cybersecurity Breach from MOVEit Exploit
SecurityScorecard conducted an extensive investigation into the Zellis breach. This research revealed alarming insights about the scale and persistence of the attack. The data exfiltration was carried out in several steps: Netflow data from Zellis IP ranges indicated large outbound transfers over HTTPS, which pointed towards the presence of a web shell. Additionally, SecurityScorecard researchers detected exfiltration over SSH to known malicious IP addresses.
What is a Third-Party Data Breach?
A data breach is an IT security incident where data is compromised or stolen from a system without the knowledge or authorization of its owner. But what happens when a third party is involved? Stolen data may include sensitive, proprietary, or confidential information such as credit card numbers, trade secrets, customer, or patient data. Third party breaches cost millions of dollars every year to companies of all sizes.
How To Identify Internal Control Weaknesses
Announcing Insights: Helping you focus on top risks for your organization
Modern applications are built, deployed and, run in increasingly complex and dynamic environments. Assessing and prioritizing the security issues introduced by these applications without taking this context into account inevitably leads to focusing remediation efforts on the wrong set of issues. This not only results in real risk slipping under the radar but also wastes the valuable time of developers, increasing their frustration and eroding their trust in security.
Attack Surface Intelligence (ASI) Data Updates: Enhancing Threat Research Capabilities
In the ever-evolving cybersecurity landscape, staying ahead of potential threats is crucial. Attack Surface Intelligence (ASI) is vital in identifying vulnerabilities and mitigating risks. This blog post will discuss the latest data updates in ASI and the exciting developments within our threat research group.
The Meal Planner's Guide to Cyber Risk
Obrela - Manage Detection and Response
Managing technology risk
Numerous risks are inherent in the technologies that all organizations use. These risks have especially become apparent with recent ransomware attacks, which have crippled major infrastructure such as the Colonial Pipeline in the Eastern United States1. This discussion will focus on how GRC, or governance, risk, and compliance can help organizations face and manage the risks that they face.
How to Establish a Cybersecurity Baseline That Works for Your Organization
A cybersecurity baseline is an invaluable set of standards for your organization. It helps you understand your security posture, identify security gaps, and meet cybersecurity regulations. The most widely adopted cybersecurity baselines are those recommended by the NIST Cybersecurity Framework, the SANS Top 20 Critical Security Controls, and Shared Assessments (designed for third-party risk management). We covered the specifics of these frameworks in a previous blog.
5 Tips for Crafting a Cybersecurity Risk Remediation Plan
With the new year upon us, now is the ideal time to re-evaluate your cybersecurity controls and your cybersecurity risk remediation strategy. Do you have a plan for cybersecurity risk remediation? Has this plan outlined who needs to be involved? How are you being notified of risks? Is there a process in place to identify and prioritize the riskiest threats for rapid remediation? This year, plan ahead for evolving cybersecurity threats and follow these five tips for crafting a risk remediation plan.
Why Security Awareness Training Does Not Equal Security Behaviour Change
Is Security Awareness and Training the 2nd Class Citizen of Cyber Security?
Presenting Accurate Security Behaviour Data to the Board
What the Future of Human Risk Management Looks Like
Measure Actual Security Behaviour Change, Not training Completion
My Vendor Doesn't Have a SOC Report, How Do I Assess Them?
More Network Security Monitoring Tools Doesn't Mean More Visibility
Network security monitoring tools are a critical component of any IT security toolkit. These tools help protect your network from online threats by looking for weaknesses and potential dangers in your organization's digital properties. But as digital ecosystems have expanded into the cloud, remote locations, and across geographies – the number of monitoring tools has skyrocketed.
Evolving Trends in the Cyber Insurance Market
Cyber insurance is the fastest-growing sector of the world’s insurance markets. But, a recent increase in ransomware attacks and business email compromises has led to a sharp uptick in claims, resulting in significant losses for cyber insurers and increased premiums. Cyber insurance customers need a way to increase their cyber resilience, reduce premiums, and improve their cyber postures.
11 Proven Risk Mitigation Strategies
Cyber Risk Protection and Resilience Planning for Boards
Cybersecurity is a top risk for corporate directors to understand and navigate. The implications of cyber events for a company are many and growing: instantly damaged reputations that erode years of credibility and trust with customers and investors, impaired profitability from customer attrition and increased operating costs, lost intellectual property, fines and litigation, and harm to a company’s people and culture.
How to Communicate Third-Party Risk to the Board in 2023
ISO 9000 vs ISO 9001
How to Measure and Communicate Cybersecurity Progress
Last week, SecurityScorecard was invited to participate in a fireside chat with Michael Daniel, President & CEO of the Cyber Threat Alliance (CTA). SecurityScorecard’s Chief Business Officer, Sachin Bansal, joined Daniel for a lively discussion regarding how to measure cyber health and clearly communicate progress against those metrics.
7 Vendor Risk Assessment Tips
Organizations rely on dozens or hundreds of third-party vendors every day to provide strategic services. Due to the increased reliance on outsourcing, the need to automatically and continuously monitor and manage vendors is not an option—it’s a business imperative. As the frequency and severity of third-party data breaches continue to escalate, your organization must remain vigilant so it can effectively protect its network and data from cyberattacks.