- January 2025 (11)
- December 2024 (17)
- November 2024 (11)
- October 2024 (14)
- September 2024 (22)
- August 2024 (14)
- July 2024 (23)
- June 2024 (22)
- May 2024 (15)
- April 2024 (19)
- March 2024 (12)
- February 2024 (20)
- January 2024 (18)
- December 2023 (15)
- November 2023 (15)
- October 2023 (13)
- September 2023 (14)
- August 2023 (18)
- July 2023 (24)
- June 2023 (19)
- May 2023 (17)
- April 2023 (17)
- March 2023 (22)
- February 2023 (23)
- January 2023 (14)
- December 2022 (19)
- November 2022 (16)
- October 2022 (23)
- September 2022 (22)
- August 2022 (14)
- July 2022 (9)
- June 2022 (11)
- May 2022 (12)
- April 2022 (17)
- March 2022 (13)
- February 2022 (9)
- January 2022 (10)
- December 2021 (13)
- November 2021 (16)
- October 2021 (6)
- September 2021 (8)
- May 2021 (2)
- November 2020 (2)
- August 2020 (1)
- November 2019 (1)
- August 2019 (1)
- March 2017 (2)
Cybersecurity is a field that requires 24x7 vigilance and constant adaptation. Arctic Wolf’s cloud native platform and Concierge Security® Team delivers uniquely effective solutions.
The cybersecurity industry has an effectiveness problem. New technologies, vendors, and solutions emerge every year—yet, we still see headlines filled with high-profile breaches. Many attacks occur – not because a product failed to raise an alert – they fail because the alert was missed or was not actioned on. To prevent these attacks, the industry needs to adopt a new approach by focusing on security operations. That’s where Arctic Wolf can help.
Arctic Wolf® Platform
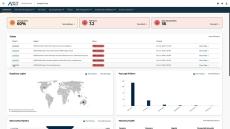
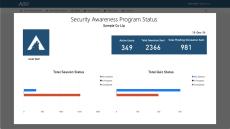
Spanning thousands of installations, the Arctic Wolf® Platform processes over 200 billion security events daily. The platform collects and enriches endpoint, network, and cloud telemetry, and then analyzes it with multiple detection engines. Machine learning and custom detection rules then deliver personalized protection for your organization.
While other products have limited visibility, the vendor-neutral Arctic Wolf® Platform enables broad visibility and works seamlessly with existing technology stacks, making it easy to adopt while eliminating blind spots and vendor lock-in.
Concierge Security® Team
Arctic Wolf invented the concept of Concierge Security®. With this delivery model, we pair a team of our security operations experts directly with your IT or security staff. Your Concierge Security® Team gives you 24×7 eyes-on-glass coverage. We work with your team on an ongoing basis to learn your security needs so that they can tune solutions for maximum effectiveness and ensure that your security posture gets stronger over time.
The Concierge Security® Team combines deep security operations expertise with an understanding of your environment to deliver better outcomes. We take on tactical actions like threat hunting and alert prioritization, and strategic tasks like security posture reviews and risk management.