The Ultimate Guide to Building and Publishing Modern npm Packages (PART 1)
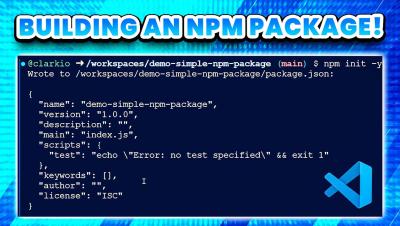
In this video, we’ll walk you through the process of creating a modern npm package from scratch. Whether you're a seasoned developer or just starting out, this step-by-step guide will show you how to build, test, and publish an npm package.