Overcoming Network Migration Challenges with Forward Networks
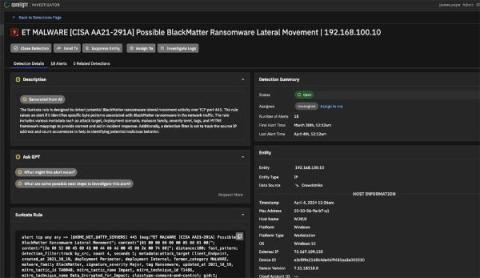
Network migration is a critical undertaking for any organization looking to optimize their network performance, adopt new technologies, or achieve cost savings. However, this process poses numerous challenges that can lead to disruptions and unwarranted risks if not properly managed.