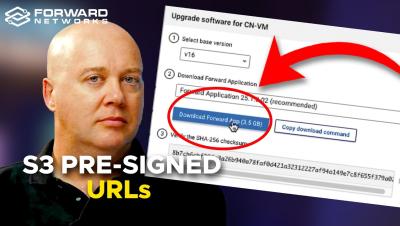
A Guide to S3 Pre-Signed URLs: What They Are and How They Work
This guide explores S3 pre-signed URLs, explaining their purpose, benefits, and how they function. It also includes a demonstration of creating and using pre-signed URLs in the AWS Management Console and highlights their integration within the Forward Networks platform for secure and efficient workflows.