Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Product Release
Unlock 1Password with Duo, OneLogin, and more
1Password Business customers can now unlock 1Password with identity providers (IdPs) that support the generic OpenID Connect (OIDC) configuration like Duo, OneLogin, JumpCloud, and others.
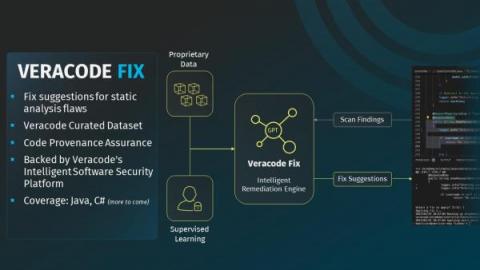
How to Measurably Reduce Software Security Risk with Veracode Fix
Veracode Fix is now available as an add-on to Veracode Static Analysis for customers on the North American instance. Availability for customers on Veracode’s EMEA and FedRAMP instances will be coming soon!
What's new in Calico Enterprise 3.17: Namespace isolation, WireGuard support for AKS and EKS, and more!
We are excited to introduce the early preview releases for Calico Enterprise 3.17. This release focuses on helping enterprises have a strong security posture for their containers and Kubernetes clusters. Let’s go through some of the highlights of this release.
Rolling out our privacy-preserving telemetry system
Back in March, we shared our plan to develop a privacy-preserving telemetry system that will help us build an even better 1Password. The goal was simple: to better understand how people are using 1Password, where they’re getting stuck, and which updates we should be focusing on first.
Introducing the Tines Toolkit
Hello friends, it’s Troy, your friendly neighborhood automation engineer, here to guide you through a really cool feature, or product-within-our-product, which is the Tines Toolkit. We launched the toolkit back in May, and this guide will help you navigate the features available today.
Introducing Compliance Score: simplifying compliance assessment
Introducing Bearer Cloud
Today, we're pleased to announce a new approach to help teams manage application code security at scale supercharged with deep sensitive data context, and ship trustworthy products faster.
New Integration Between NC Protect and Janusseal Offers Robust Classification and Dynamic Data Protection for Customers
Salt Announces Bi-directional Integration with Wiz!
We have exciting news to share! Salt Security is building a bi-directional integration with the Wiz cloud security platform! With this announcement, Salt becomes the first API security vendor to build a two-way integration with Wiz, giving Wiz customers the deepest and most actionable insights into API behaviors – all within Wiz’s comprehensive cloud security platform.