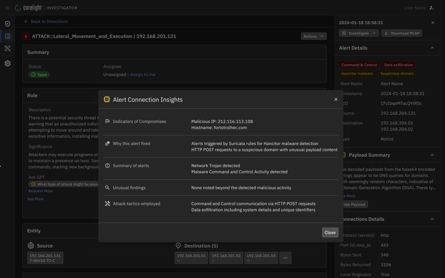
A New Era In Human Risk Management:Introducing KnowBe4 HRM+
Cybersecurity threats grow more sophisticated by the day. Amid this constant change, one truth remains: people are simultaneously our greatest security vulnerability and our strongest line of defense. It’s time to empower organizations with a new approach that minimizes human risk and maximizes protection.