|
By Mike Horn
The threat landscape is constantly evolving and expanding, making it more difficult than ever for organizations to keep up and defend against the latest threats. Today’s SecOps teams need cutting-edge security tools and threat intelligence-driven detection content to proactively defend against the latest tactics, techniques and procedures (TTPs) that organizations face today.
|
By Mick Baccio
In today’s digital age, achieving cyber resilience is no longer an option—it has become a necessity. Yet, according to the latest report by Splunk, conducted in collaboration with Foundry, a significant cyber confidence gap exists among public sector organizations in this critical area.
|
By Muhammad Raza
As organizations face the imminent threat of an IT service outage or cyberattack, they often fail to step back and understand how well they've planned to deal with the crisis. According to recent research, we know that: Perhaps the most regrettable part of it all? Almost half (45%) of these organizations already acknowledge the inadequacy of their disaster recovery capabilities.
|
By Muhammad Raza
In the realm of cybersecurity, understanding how unauthorized access can compromise sensitive systems is critical—this is where the concept of privilege escalation comes into play. In this article, we will look at what privilege escalation is, how it exploits vulnerabilities and best practices for protecting your organization against privilege escalation.
|
By Michael Haag
The e-commerce world was recently shaken by the discovery of a vulnerability in Adobe Commerce and Magento, two of the most widely used e-commerce platforms. Dubbed "CosmicSting" and designated as CVE-2024-34102, this vulnerability exposes millions of online stores to potential remote code execution and data exfiltration risks.
|
By Michael Haag
In September 27, 2024, Okta disclosed a critical vulnerability affecting their Classic environment that created a concerning security gap in identity protection. The vulnerability, active since July 17, 2024, allowed attackers with valid credentials to bypass application-specific sign-on policies by simply modifying their user-agent string.
Braodo Stealer is one of the many active and evolving malware families designed to steal sensitive information, such as credentials, cookies, and system data, from compromised machines. Typically written in Python, this malware employs a variety of obfuscation techniques to conceal its true intentions, making it challenging for security solutions to identify.
|
By John Dominguez
Data is everywhere, sprawling across cloud, on-premises, and hybrid environments. As security practitioners, we need fast access to this data to analyze it, draw insights, and uncover potential threats. However, the sheer volume of data and complexity of threats makes it difficult to maintain visibility, detect stealthy attacks, and respond quickly to security incidents.
|
By John Dominguez
Security teams are juggling 25+ different security tools that perform different actions across detection, investigation and response. Look up an IP here, send malware to a sandbox there, block an executable over there. What’s worse is that the vast majority of those actions are being performed manually. This approach is simply too slow against fast-moving attackers and malware, and it certainly isn’t sustainable.
|
By Olivia Henderson
At.conf24 we unveiled the private preview of Splunk Enterprise Security 8.0, and the buzz was undeniable. Today, we are thrilled to announce that Splunk Enterprise Security 8.0 is now generally available! This isn’t just another release—it’s a massive leap forward that redefines and revolutionizes security operations. Splunk Enterprise Security 8.0 is the cornerstone of the SOC of the Future.
|
By Splunk
Federated Analytics gives organizations the full power of Splunk extended to data stored in Amazon Security Lake. Trusted partners like Accenture are helping bring these new capabilities to life at organizations around the world.
|
By Splunk
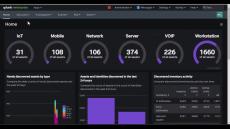
Learn how Splunk Asset and Risk Intelligence can help you identify and close gaps in security controls and validate compliance status with out-of-the-box and customizable dashboards and metrics.
|
By Splunk
If you haven't already, say hello to Splunk Enterprise Security 8.0.
|
By Splunk
IT environments are more complex than ever, with data scattered across multiple sources. Splunk’s data management and federation capabilities provide efficient, cost-effective ways to control, shape, and access data in real-time. Ensure visibility, security, and compliance while optimizing costs. Manage your data at scale and access it wherever it resides with Splunk’s flexible tools.
|
By Splunk
In Splunk SOAR 6.3, SOAR features now come fully integrated with Splunk Enterprise Security 8.0. In this demo, see how to easily create a Splunk SOAR playbook in the context of your SIEM workflows. Playbooks and actions are now directly integrated within the Splunk Enterprise Security analyst queue. You can run playbooks and see the results without leaving the Splunk Enterprise Security interface. Both a Splunk SOAR and Splunk Enterprise Security license is required.
|
By Splunk
Prompt-driven automation in Splunk SOAR 6.3 lets you send real-time, secure prompts to teams outside the SOC to streamline response workflows and resolve security incidents faster. Deliver prompts through any ITOps, ChatOps or Ticketing applications.
|
By Splunk
With Splunk SOAR, analysts can rise above drowning alert noise, focus on key security objectives and always stay ahead of evolving threats.
|
By Splunk
Learn how Splunk Enterprise Security empowers SOC efficiency with coordinated workflows and unifies processes across threat detection, investigation and response.
|
By Splunk
Learn how the asset inventory provided by Splunk Asset and Risk Intelligence delivers a much-needed source of truth, bringing together different sources, helping to discover previously unknown assets, and delivering context and enrichment for key cybersecurity activities.
|
By Splunk
The hype around artificial intelligence (AI) and machine learning (ML) has exploded, sometimes overshadowing the real uses and innovations happening everyday at organizations across the globe. The reality is that applying AI and ML to data-dependent challenges presents opportunity for better security, faster innovation and overall improved efficiency.
|
By Splunk
Do you have a plan for cybersecurity? Digital technology is touching every aspect of our lives, which is giving bad actors unlimited runway to create new threats daily. It's this atmosphere that makes it imperative that organizations are prepared, informed and actively hunting for adversaries.
|
By Splunk
Cyberattacks are top of mind for organizations across the globe. In fact, 62 percent of firms are being attacked at least weekly and 45 percent are experiencing a rise in the number of security threats. But do organizations have the processes in place to investigate and effectively respond to these incidents? IDC recently surveyed security decision makers at 600 organizations to understand the state of security operations today.
|
By Splunk
How can you utilize machine data to be prepared for the General Data Protection Regulation of the European Union?
|
By Splunk
A security information event management (SIEM) solution is like a radar system that pilots and air traffic controllers use. Without one, enterprise IT is flying blind. Although security appliances and system software are good at catching and logging isolated attacks and anomalous behavior, today's most serious threats are distributed, acting in concert across multiple systems and using advanced evasion techniques to avoid detection.
|
By Splunk
Security incidents can happen without warning and they often go undetected for long periods of time. Organizations struggle to identify incidents because they often work in silos or because the amount of alerts is overwhelming and hard to determine the signals among the noise.
|
By Splunk
All data is security relevant and defending against threats involves every department in a company. With cyberthreats and bad actors constantly evolving, it is imperative for everyone in an organization to come together to identify and protect critical data.
|
By Splunk
Recent cyberattacks have made it clear that organizations of all sizes need to focus on a holistic and cohesive security strategy. Security operations centers (SOCs) have become a focal point in this effort, consolidating the right people, processes and technology to mitigate and remediate attacks.
|
By Splunk
Current IT security tools and mindsets are no longer adequate to meet the scope and complexity of today's threats. Internet security has evolved over the last ten years but advanced persistent threats and the sophistication of the malware have fundamentally changed the way security teams must think about these new threats and the tools used for detective controls.
- February 2025 (1)
- January 2025 (1)
- December 2024 (4)
- November 2024 (9)
- October 2024 (13)
- September 2024 (10)
- August 2024 (11)
- July 2024 (7)
- June 2024 (6)
- May 2024 (7)
- April 2024 (7)
- March 2024 (11)
- February 2024 (13)
- January 2024 (21)
- December 2023 (21)
- November 2023 (11)
- October 2023 (27)
- September 2023 (24)
- August 2023 (25)
- July 2023 (22)
- June 2023 (37)
- May 2023 (32)
- April 2023 (32)
- March 2023 (35)
- February 2023 (19)
- January 2023 (21)
- December 2022 (9)
- November 2022 (19)
- October 2022 (12)
- September 2022 (8)
- August 2022 (14)
- July 2022 (8)
- June 2022 (7)
- May 2022 (13)
- April 2022 (11)
- March 2022 (7)
- February 2022 (2)
- January 2022 (9)
- December 2021 (14)
- November 2021 (23)
- October 2021 (12)
- September 2021 (16)
- August 2021 (14)
- July 2021 (20)
- June 2021 (17)
- May 2021 (6)
- April 2021 (10)
- March 2021 (15)
- February 2021 (10)
- January 2021 (5)
- December 2020 (4)
- November 2020 (9)
- October 2020 (6)
- September 2020 (6)
- August 2020 (7)
- July 2020 (10)
- June 2020 (3)
- May 2020 (9)
- April 2020 (13)
- March 2020 (5)
- February 2020 (6)
- January 2020 (5)
- December 2019 (1)
- October 2019 (1)
- May 2019 (1)
- October 2018 (1)
- June 2018 (2)
- May 2018 (1)
- April 2018 (2)
- March 2018 (1)
- February 2018 (1)
- January 2018 (1)
Splunk produces software for searching, monitoring, and analyzing machine-generated big data, via a Web-style interface.
Splunk turns machine data into answers. Regardless of your organization’s size and industry, Splunk can give you the answers you need to solve your toughest IT, security and business challenges—with the option to deploy on-premises, in the cloud or via a hybrid approach.
Work the Way Your Data Works:
- Real-Time: Splunk gives you the real-time answers you need to meet customer expectations and business goals.
- Machine Data: Use Splunk to connect your machine data and gain insights into opportunities and risks for your business.
- Scale: Splunk scales to meet modern data needs — embrace the complexity, get the answers.
- AI and Machine Learning: Leverage artificial intelligence (AI) powered by machine learning for actionable and predictive insights.
Any Question. Any Data. One Splunk.