SIEM in Seconds - Splunk Enterprise Security Auto Refresh and Timeline of Notable Events
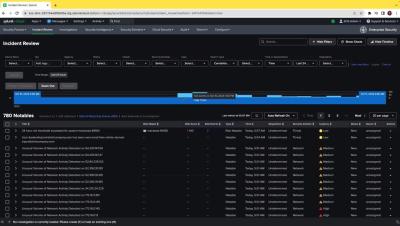
SOC analysts are overwhelmed sifting through a sea of notable events. They are unable to prioritize events and act fast. With Auto Refresh in the Incident Review interface, users will not have to re-run the Incident Response search or refresh the page. Furthermore, an interactive timeline for notable events within the Incident Response interface enables the SOC to quickly prioritize critical incidents.