Hyperledger Fabric Security Monitoring with Splunk
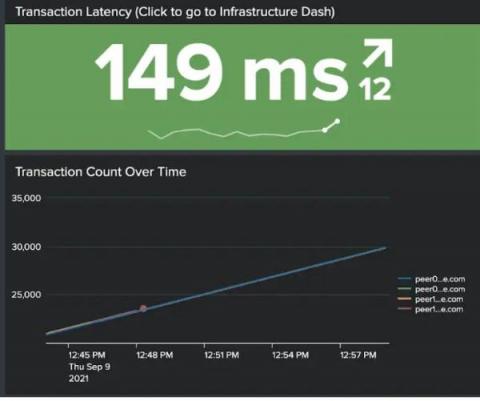
In this post, we demonstrate how to set up effective security monitoring of your Hyperledger Fabric infrastructure. We identify some common threats, recognize key data sources to monitor, and walk through using Splunk to ingest and visualize your data. This post follows Introducing Splunk App for Hyperledger Fabric and highlights the use of the app for security monitoring of blockchain infrastructure. We will address smart contract/chaincode security & monitoring in a follow-up post.