CIO POV: Five Essential Themes Shaping the CIO's Tech Agenda
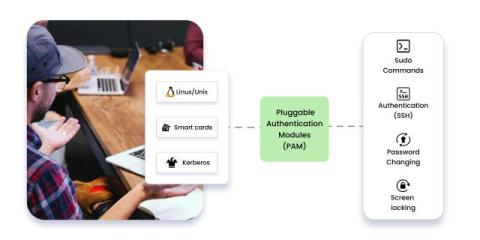
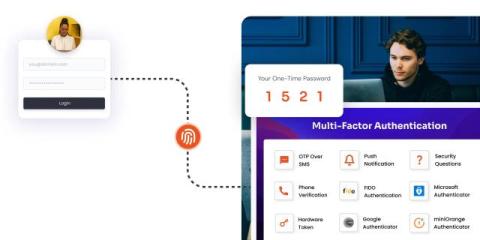
Technology is rapidly redefining how we live and work. As CIO at CyberArk, I often get asked about the themes and realities shaping today’s tech agenda. Some of them—I’m looking at you, AI—are shiny and hyped, while others are familiar and fundamental yet equally important. Here’s a look at five on the top of my list.