|
By miniOrange
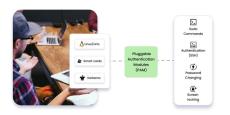
Discover the Pluggable Authentication Modules (PAM) framework in UNIX & Linux. Learn how PAM enables seamless integration of diverse authentication modules.
|
By miniOrange
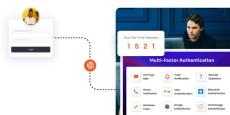
The EU is making active efforts to secure the citizens and their data. New laws are implemented and as a compliance, MFA is mandated for enterprises.
|
By miniOrange
Discover the benefits, challenges, and key features of cloud-based access control, a scalable and secure solution for modern organizations to manage access remotely.
|
By miniOrange
Know how security assertion markup language, SAML works to exchange authentication and authorization data in web domain security in XML format.
|
By miniOrange
Is your team struggling to manage work apps on personal Android devices? Switching between emails, work chats, and personal messages can be frustrating and time-consuming. Fortunately, Android offers a solution called “Work Profile” that keeps business apps separate from personal ones—boosting productivity while maintaining security.
|
By miniOrange
Are your employees accessing restricted websites during work hours? Unrestricted web access on company devices can lead to decreased productivity and increased security risks. For businesses, controlling online activity on work-issued Android phones and tablets is essential to maintaining a secure and focused work environment.
|
By miniOrange
Passwordless SSO enables users to securely access multiple applications with a single sign-on, without needing passwords.
|
By miniOrange
Do you ever wish you could lock your Android device to a single app or restrict specific functions for a more focused and secure experience? Guided Access can make it happen. This blog will guide you through everything you need to know about enabling Guided Access for Android devices, its benefits, and how miniOrange MDM can take it to the next level.
|
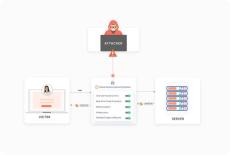
By miniOrange
Are your users sessions truly secure? Learn how session hijacking via cookie manipulation impacts businesses. Discover the power of CASB solutions in tackling these threats.
|
By miniOrange
Discover how to enhance your Joomla site’s security and streamline user authentication with OAuth.
|
By miniOrange
Lokesh Singh Rajawat, Senior Software Engineer at miniOrange, delivers an engaging session on establishing foundational cybersecurity practices. Gain insights into crafting resilient security frameworks that serve as the cornerstone of modern cyber defense strategies, protecting against evolving threats in today’s digital landscape.
|
By miniOrange
In this insightful session, Vipika Kotangale, Technical Content Writer at miniOrange, delves into the world of AI-driven identity scams and shares actionable strategies to safeguard your personal and organizational data. Learn how to identify and counter AI-generated phishing attempts, protect sensitive information, and stay ahead of cybercriminals in an era of evolving threats.
|
By miniOrange
Join Dhruv Bhavsar as he explores the endpoint security lifecycle, from deployment to decommissioning. Learn to address challenges like BYOD, compliance, and diverse devices while leveraging Zero Trust and AI-driven solutions. Discover strategies to enhance your organization’s security posture and mitigate threats effectively.
|
By miniOrange
In an exclusive interview at the IdentityShield Summit '25, Anirban Mukherji, Founder & CEO of miniOrange, shares the inspiring journey behind miniOrange's rise in the cybersecurity industry. From overcoming challenges to delivering innovative solutions, discover the story of passion, vision, and dedication that led to miniOrange becoming a leader in identity and access management. Watch now for insights and inspiration!
|
By miniOrange
Protect Your WordPress Site with miniOrange Two-Factor Authentication (2FA)! miniOrange’s Two-Factor Authentication (2FA) provides an extra layer of security to keep your data safe from unauthorized access. Our 2FA solution is simple, reliable, and user-friendly, ensuring only verified users can log in to your site. With more than 15+ 2FA options like OTP over SMS/email, and authenticator apps, you can choose the method that works best for you.
|
By miniOrange
This video will walk you through the steps required to configure PingOne as an Identity Provider and Drupal as a Service Provider. The module allows users to log in to the Drupal site using their PingOne account.
|
By miniOrange
In this webinar recording, explore how Identity and Access Management (IAM) and Privileged Access Management (PAM) solutions empower organizations to achieve compliance with the Essential Eight framework, bolstering cybersecurity in the Australian landscape. What you’ll learn: How IAM and PAM support Essential Eight compliance. Real-world examples of strengthening cybersecurity. Insights into streamlining access management. Live Q&A highlights with industry experts.
|
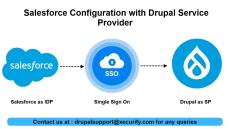
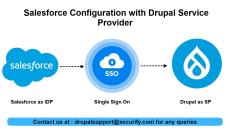
By miniOrange
This video will walk you through the steps required to configure Salesforce as an Identity Provider and Drupal as a Service Provider. The module allows users to log in to the Drupal site using their Salesforce account.
|
By miniOrange
Say Goodbye to Login Hassles with WordPress SSO! Tired of remembering multiple passwords on your WordPress site? With miniOrange's Hide and Disable WordPress Login feature, you can completely hide the default login form and implement a Single Sign-On WordPress option with your preferred Identity Provider. This game-changing solution not only simplifies access but also elevates your WordPress admin login security.
|
By miniOrange
This video will walk you through the steps required to configure Okta as an Identity Provider and Drupal as a Service Provider. The module allows users to log in to the Drupal site using their Okta account. Chapters: Don't forget to subscribe to our channel and click on a bell icon to get notifications about new uploads.
- February 2025 (7)
- January 2025 (15)
- December 2024 (9)
- November 2024 (8)
- October 2024 (13)
- September 2024 (20)
- August 2024 (5)
- May 2024 (1)
Get industry-leading security solutions for your employees, customer, and partner to enhance productivity, frictionless user experience, and increased customer sign-ups.
miniOrange is a world-class cybersecurity organization that has been delivering innovative products in the cybersecurity space for over a decade. With a focus on Identity and Access Management (IAM) and Customer Identity and Access Management (CIAM), we offer cutting-edge solutions to secure your workforce, customers, and partners.
Secure Digital Experience for your Workforce:
- Frictionless Secure Login: Avoid the burden of signing in and out many times for app access of users abd business partners and improve your Workforce Productivity.
- Remote Workforce Access: Secure Identities of remote users and get secure access to tools and devices they require in a timely manner from any location – without compromising security.
- Security with ease: Use our services to manage workforce identities without a second thought. Let us worry about the Security and Privacy of your workforce identities.
- Migrate and reduce IT Friction: Reduce your costs by migrating to the cloud and enhancing your workforce or business resources.
- Improve Business Agility: Organize Identity and Access Management (IAM) solutions that can be adopted, managed easily and used by the workforce right away.
Customer Identity & Access Management (CIAM):
- Redefine Customer Experience: Enable your customers to enjoy effortless access from anywhere, anytime, on any device with seamless authentication methods like Single Sign-On (SSO), Passwordless Login, Social Login, etc. Provide customized recommendations, targeted promotions, and personalized content by leveraging comprehensive customer profiles provided by our CIAM platform and foster better customer engagement.
- Secure Your Customer Accounts & Manage Access: Prioritize the security of customer accounts by implementing robust authentication mechanisms, including MFA and Adaptive MFA. With our CIAM platform, enable 2FA with 15+ MFA methods to choose from. Streamline the onboarding process by automating the provisioning of customer accounts, granting immediate access to the necessary resources.
- Ask for Consent & Comply with Regulations: Enable customers to have full control over their personal information by providing transparency and easy-to-use privacy & consent management tools. Easily comply with requirements of data protection regulations like the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), etc., and earn higher brand credibility. Know more about other compliance.