A Deep Dive into DeepSeek
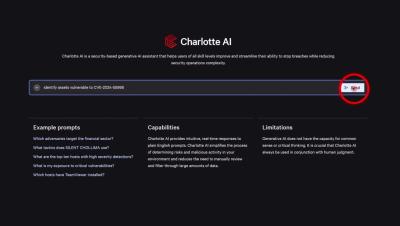
At a time when new AI models are constantly emerging, the launch of DeepSeek has led to questions and concerns around AI model security, data security, and national security. What is DeepSeek, and how was it trained? What are the risk implications of using it? Tune in for the answers to these questions and more in our first-ever video episode of the Adversary Universe podcast.