Security
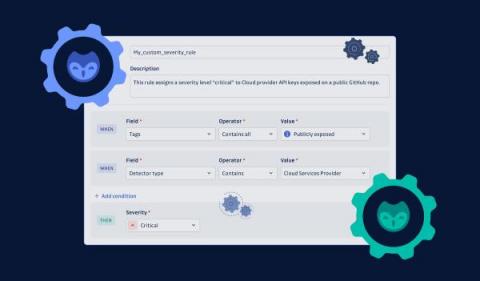
Create and manage severity rules. Supercharge your remediation.
Tweak our default severity rules or create new ones and align GitGuardian’s automated severity scoring engine with your organization’s security priorities!
How To Communicate Attack Surface Management to the Board
CVE-2023-33733: RCE Vulnerability in ReportLab PDF Toolkit
Protect Your Private Packages With GitGuardian Honeytoken
My Vendor Doesn't Have a SOC Report, How Do I Assess Them?
Exploring the World of DevRel and Security: BoxyHQ AMA with Aldin Kiselica from Cerbos
Evolving Trends in the Cyber Insurance Market
Cyber insurance is the fastest-growing sector of the world’s insurance markets. But, a recent increase in ransomware attacks and business email compromises has led to a sharp uptick in claims, resulting in significant losses for cyber insurers and increased premiums. Cyber insurance customers need a way to increase their cyber resilience, reduce premiums, and improve their cyber postures.
Vulnerability prediction insights from Outpost24 on Smashing Security
The Smashing Security podcast recently invited our Director of Product Management, John Stock, on to discuss our Vulnerability Prediction Technology (VPT) tool, the security challenges brought by remote work, and the importance of balancing risk management with business goals.
What Is a Pretexting Attack?
A pretexting attack is a type of social engineering attack where the threat actor persuades their target into revealing sensitive information or sending them money by making up a story, hence the word “pretext.” Pretexting attacks can come in many different forms including a phone call, text message, email or even in person.