Dissecting Buffer Overflow Attacks in MongoDB
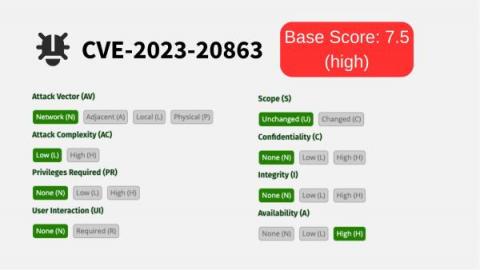
Towards the end of 2020, a new vulnerability in MongoDB was found and published. The vulnerability affected almost all versions of MongoDB, up to v4.5.0, but was discussed and patched appropriately. The vulnerability, CVE-2020-7928, abuses a well-known component of MongoDB, known as the Handler, to carry out buffer overflow attacks by way of null-byte injections.