Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
opsdemon
Latest posts
Tigera: Troubleshoot Kubernetes Networking Issues and Implement Effective Network Policies
Are networking challenges disrupting your Kubernetes environment? Denied flows, DNS errors, latency issues, and policy misconfigurations can cause serious disruptions and potential security breaches in your clusters. Without the right container networking and security solution, these problems can significantly impact your operations.
Resecurity introduces Government Security Operations Center (GSOC) at NATO Edge 2024
Resecurity, a global leader in cybersecurity solutions, unveiled its advanced Government Security Operations Center (GSOC) during NATO Edge 2024, the NATO Communications and Information Agency's flagship conference. The solution is also specifically tailored for MSSPs that protect aerospace and defense organizations.
DMD Diamond Launches Open Beta for v4 Blockchain Ahead of 2025 Mainnet
DMD Diamond - one of the oldest blockchain projects in the space has announced the start of Open Beta for the DMD Diamond v4 blockchain. Established in 2013, DMD Diamond is recognized as a decentralized, community-driven initiative. The v4 blockchain introduces a host of advanced features, designed to enhance efficiency and usability. Beginning December 9, the Open Beta phase invites developers and blockchain enthusiasts to test the platform's innovative functionality.
Bridging the Cyber Confidence Gap: Digital Resilience in the Public Sector
In today’s digital age, achieving cyber resilience is no longer an option—it has become a necessity. Yet, according to the latest report by Splunk, conducted in collaboration with Foundry, a significant cyber confidence gap exists among public sector organizations in this critical area.
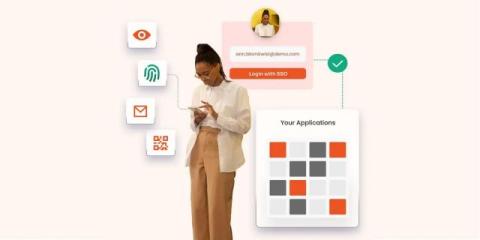
What are Single Sign-On (SSO) Examples?
Derive practical insights from the best SSO examples for use cases in different industries and functionalities to achieve secure single sign-on.
Alert Fatigue: How Can NDR Help?
Alert fatigue is the process of burning out and losing sensitivity to security alerts caused by a deluge of security alerts. Security systems generate a constant flow of alerts in modern network environments, ranging from minor irregularities to severe threats. But not all these alerts are equal in importance, and many of them are false positive alerts or low-priority problems.
Trustwave's 2025 Cybersecurity Predictions: The Rise of Generative AI Data Breaches, Quantum Computing, and Cyber Warfare
As we look ahead to 2025, the cybersecurity landscape is poised for significant shifts and challenges. Here are some key predictions that I believe will take place or start to happen in the coming year.
How Fidelis NDR Stands Out: Deep Session Inspection Explained
Discover how Fidelis Network Detection and Response (NDR) goes beyond traditional Deep Packet Inspection (DPI) systems. In this insightful video, we explore how Fidelis NDR provides unparalleled visibility into network traffic, enabling organizations to detect and analyze sensitive data within complex, multi-level archive files and beyond. Key highlights include: Watch to see how Fidelis NDR empowers proactive cybersecurity through advanced data visibility and inspection techniques.
Challenges with Data Security Posture Management (DSPM)
While Data Security Posture Management (DSPM) is a powerful approach for discovering, monitoring, and managing sensitive data across complex systems, it is not without its challenges. These hurdles often stem from the complexity of modern data environments, evolving threats, and operational constraints. Below are the primary challenges associated with DSPM.