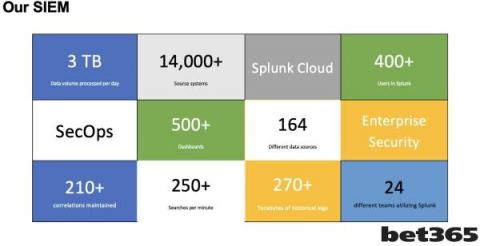
Inside the SecOps Team at bet365: Moving your SIEM to the Cloud
Hello, I love to look behind the scenes of SecOps teams to learn how they operate. Recently I had the pleasure to work with John Eccleshare, Head of Compliance and Information Security, at bet365 as John took the stage at Gartner Security and Risk Summit in London.