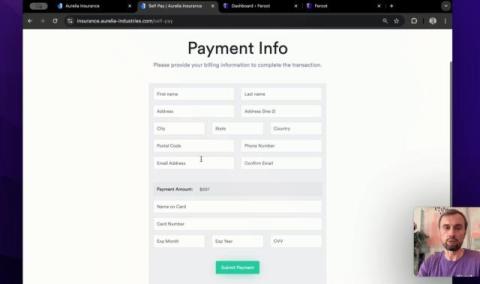
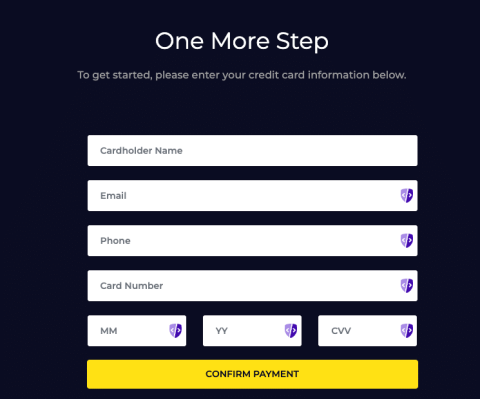
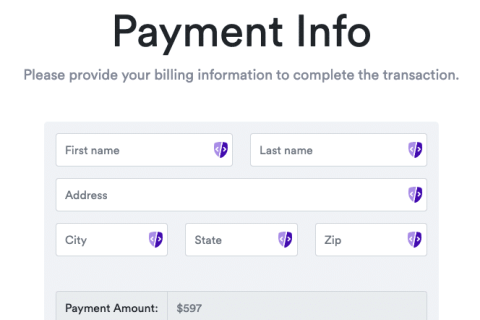
Is Your Hospital Sharing Patient Data with Facebook? A Guide for Security and Privacy Teams
Recent lawsuits have revealed a critical privacy concern for healthcare providers – the sharing of patient data with Facebook through tracking pixels. We wrote this article to help your security and privacy teams assess their risk, identify key stakeholders, and understand the urgency of this issue.