Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
JavaScript
Stranger Danger: Your JavaScript Attack Surface Just Got Bigger
How to write your first unit test in JavaScript
Testing code is the first step to making it secure. One of the best ways to do this is to use unit tests, ensuring that each of the smaller functions within an app behave as they should — especially when the app receives edge-case or invalid inputs, or inputs that are potentially harmful.
Introduction to JavaScript Fuzzing | How to Write a Fuzz Test With Jazzer.js
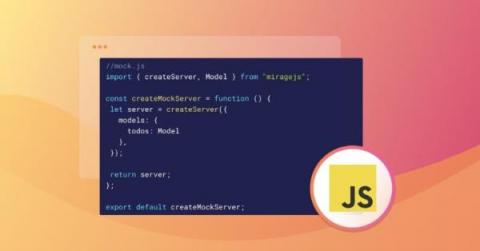
How to make a mock API server in JavaScript
Developing and testing a frontend feature can be difficult, especially when the backend it depends on is not ready. This dependency on a backend API often slows down the development process. In scenarios like this, developing a mock API can save you a lot of time by allowing you to develop your feature independent of the backend, and make it easier to test and identify scenarios where your API might fail before it is ready.
Secure JavaScript URL validation
When developers need to handle URLs in different forms for different purposes — such as browser history navigation, anchored targets, query parameters, and so on — we often turn to Java. However, its frequent use motivates attackers to exploit its vulnerabilities. This risk of exploitation is why we must implement URL validation in our JavaScript applications.