|
By Paul Foryt
We’re excited to announce the Policy SBOM feature is now generally available to all Styra DAS customers, giving enterprises transparency and traceability into deployed authorization policies. Just like a software bill of materials (SBOM) is an inventory of the components and dependencies in a software application, a Policy SBOM is an inventory of the policy modules, including their sources, versions, and dependencies, within an Open Policy Agent (OPA) policy bundle.
|
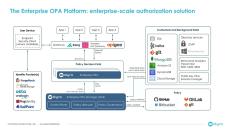
By Eric Kao
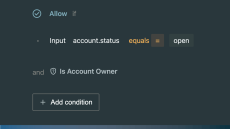
The Enterprise OPA Platform’s low-code policy builder empowers product owners and security analysts to design, review, and experiment on application permission logic directly.
|
By Anders Eknert
Summer is here, bringing thoughts of the beach, travel, and relaxation. However, summer isn’t without its chores; gardens need work, and summer houses require maintenance. Sometimes these chores can be enjoyable and even therapeutic, but most importantly, they keep our projects in good condition, allowing us to unwind and enjoy the summer months.
|
By Eric Kao
Gartner projects that by 2026, 80% of software engineering organizations will have established platform engineering teams. The vision of platform engineering is ambitious: to empower developers with all the flexibility they need while minimizing complexity. This approach has already transformed infrastructure, deployment, data analytics, encryption management, authentication, and more.
Let’s go straight to the TL;DR: we have just released a new Rego extension for the popular Zed editor! Providing both syntax highlighting and all the language server features of Regal that were previously available for editors like VS Code, or Neovim. The extension is available from the Zed extensions view, and you’ll find it by searching for “Rego”.
Filling in some blanks on large scale policy testing with Gusto‘s Nicholaos Mouzourakis.
|
By Tim Hinrichs
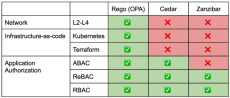
Rego, the policy language of the Open Policy Agent (OPA), is known for its flexibility and power in policy enforcement across various systems. Its declarative syntax and data-centric approach make it versatile for application authorization, infrastructure as code (IaC) authorization, and network policies. To fully appreciate OPA/Rego’s capabilities, it’s helpful to compare it with other policy languages and frameworks like AWS’s Cedar and Google’s Zanzibar.
The huge ecosystem of integrations has over time become a true differentiator for Open Policy Agent (OPA), and an embodiment of the project’s promise to provide policy across the “whole cloud native stack”. Integrating OPA into a new tech stack also tends to be a rewarding experience for developers, which might help explain why so many integrations have been provided by external contributors over the years.
|
By Tim Hinrichs
Among other things, the OWASP organization delivers reports on the Top 10 most prevalent and important security risks for web-based software development. In 2019 they started reporting on the Top 10 API Security risks and refreshed that list in 2023. In this blog we describe how OPA/Styra can help with 9 of the 10 risks, and for each one we rate how impactful OPA/Styra is: Below we detail each of these 10 risks and briefly how to address them with OPA and Styra.
|
By Charlie Egan
Relationship-based Access Control (ReBAC) is a common requirement when applying Policy as Code controls in modern applications. Consider sharing a document with a collaborator in a different organization. As the collaborator is in another organization, it might be hard to grant them a pre-defined internal role without granting more permissions than needed – if indeed an external identity can be bound to an internal role at all. This is where ReBAC comes in.
|
By Styra
Our VP of Marketing, William Chia, in a conversation with our DevRel lead Anders Eknert about the new Code Lens Evaluation feature that just landed in Regal. A conversation that quickly turns into a demo! Watch to see how the feedback loop of Rego development now is shorter than ever, and will change the way you author your policies. Rego development experience taken to a whole new level!
|
By Styra
The video discusses how policy as code creates more flexible, adaptable access control compared to the rigidity of RBAC. John Brothers from PACLabs joins Styra to share how to analyze roles and scopes, choose attributes, write policies, and roll out a successful migration.
|
By Styra
Our DevRel guru Anders Eknert, and our eminent VP of Marketing, William Chia, talk about two new features in the OPA extension for VS Code — tooltips and inlay hints for built-in functions. Both provided by Styra's linter and language server for Rego, Regal.
|
By Styra
Automatically uploaded from Zoom recording. Meeting ID:332405601.
|
By Styra
Styra Load allows you to assess the impact of policies against your current production resources. Here, Adam Sandor shows you how to use Live Impact Analysis to full effect — helping you to enforce robust policy without impacting production.
|
By Styra
Styra Load supports the Kafka API, which makes it possible to stream data updates to Styra Load. This can be useful when events representing changes to data used in policy evaluation are available on a Kafka topic. Here, Adam Sandor explains how you can use Kafta streaming data to make real-time policy decisions.
|
By Styra
Styra Solutions Architect Ádám Sándor Sandor shares how to use Styra Link to enforce Kubernetes admissions control policies using a Git-based workflow with VS Code or your CLI.
|
By Styra
Styra Developer Advocate Peter O'Neil shares how to download and install Styra Load, as well as how to hot swap Styra Load for an OPA instance.
- October 2024 (1)
- September 2024 (1)
- August 2024 (1)
- July 2024 (2)
- June 2024 (1)
- May 2024 (2)
- April 2024 (4)
- March 2024 (2)
- December 2023 (1)
- November 2023 (1)
- September 2023 (4)
- August 2023 (2)
- July 2023 (2)
- June 2023 (2)
- April 2023 (6)
- March 2023 (6)
- February 2023 (7)
- January 2023 (6)
- December 2022 (11)
- November 2022 (10)
- October 2022 (5)
- September 2022 (6)
- August 2022 (9)
- July 2022 (8)
- June 2022 (3)
- May 2022 (4)
- April 2022 (4)
- March 2022 (5)
- February 2022 (4)
- January 2022 (2)
- December 2021 (7)
- November 2021 (4)
- October 2021 (7)
- September 2021 (5)
- August 2021 (3)
- July 2021 (4)
- June 2021 (4)
- May 2021 (4)
- April 2021 (5)
- March 2021 (5)
- February 2021 (6)
- January 2021 (2)
- December 2020 (3)
- November 2020 (2)
- October 2020 (1)
- September 2020 (3)
- August 2020 (2)
- July 2020 (1)
- June 2020 (1)
- May 2020 (2)
- April 2020 (2)
- March 2020 (2)
- February 2020 (1)
- December 2019 (5)
- November 2019 (2)
- August 2019 (1)
- June 2019 (2)
- May 2019 (2)
- April 2019 (1)
- January 2019 (2)
Styra is the fastest and easiest way to put guardrails around your Kubernetes clusters--whether you’re a developer, an admin, or a bit of both.
Built on open-source, and declarative by design, Styra’s simple graphical library of customizable policies lets you easily mitigate risks, reduce human error, and accelerate development.
Security-as-code for Kubernetes:
- Declarative by design: Manually “doing security” in today’s cloud-native environments is like a never-ending game of whack-a-mole. Styra works with Kubernetes to define, enforce, and monitor desired state, and eliminate the runtime guessing game.
- Dynamic rules for dynamic environments: Simply put, Styra takes in business context, and outputs security decisions across your namespaces and clusters. Build policy-as-code directly via CLI, or with a simple point-and-click editor, and validate security before committing.
- Portable, powerful policy: Styra allows you to define policy once, then enforce wherever necessary. No more best-effort security, no more policy silos. Built on the Open Policy Agent (the leading open source policy engine), enforcement is accurate, fast, and simple.
Policy-as-code guardrails to eliminate operational, security, and compliance risk