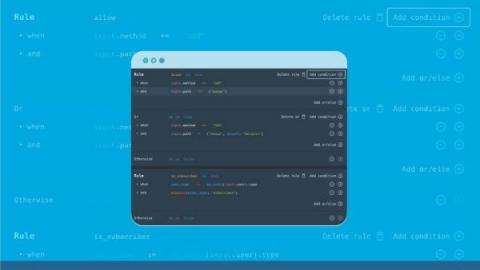
GitHub Scanning for Policy-as-Code Configuration Validation
We just enhanced Styra Declarative Authorization Service (DAS) with a feature customers have been asking for: near-instant scanning of policy-as-code config files right in GitHub. …Oh, and as a bonus, it’s free, it’s available now and it only takes a couple minutes to see live in-action in your repos!