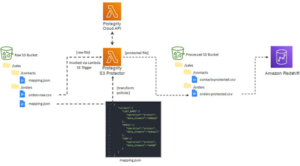
Scans required for PCI DSS compliance
As a risk-based response to the continuous, and varied assaults on our systems by criminals, the PCI DSS standard requires a minimum of 20 technical scans per full year for merchants, and 21 for third-party service providers (TPSPs)