Mastering CMMC Compliance with UTMStack: A Comprehensive and Technical Approach
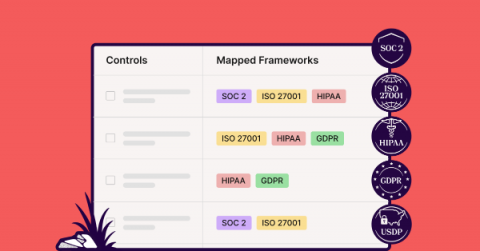
Achieving and maintaining Cybersecurity Maturity Model Certification (CMMC) compliance is a critical requirement for organizations operating within the defense industrial base. As a comprehensive SIEM solution, UTMStack offers advanced features and capabilities that not only streamline the compliance process but also inspire confidence in security and protection.