Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Compliance
Datadog achieves ISO 27701 Processor certification for customer data privacy
With the establishment of the EU General Data Protection Regulation (GDPR) and the expanding international landscape of data protection laws, organizations today face complex requirements and heightened scrutiny when it comes to data privacy. In addition, public awareness of data exploitation and digital surveillance is growing, and individuals are more concerned than ever about data privacy.
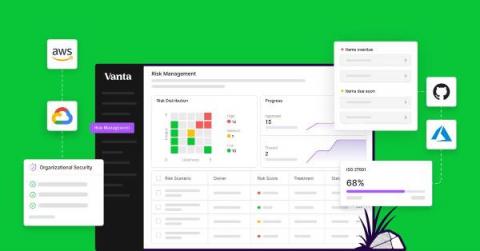
Risk Management: Addressing Shortcomings and Paving the Way Forward
In today’s ever-changing business landscape, managing risk is crucial for the success and longevity of any organization. From financial risks to operational risks and cyber threats, businesses face a range of challenges that require a robust and secure risk strategy. With the complexities of modern business, risk management can no longer be put on the back burner, and companies will need to keep up with the latest practices and solutions to stay afloat.
What is a trust management platform?
When you start pursuing compliance for a particular security standard, you do it with a specific goal in mind. Maybe you’re pursuing compliance because it’s a legal requirement in your industry or because a prospective customer requires it. But what happens after you achieve that initial SOC 2 or ISO 27001? It’s easy to get caught up in checking the boxes and lose sight of the why behind your security and compliance work.
We're one step closer to knowing how to comply with EO 14028
TrustCloud Product Updates: April 2023
Our team has been hard at work creating updates and new features just for you, see what we’ve been up to over the last month.
A Comprehensive Guide for the SOC-2 Audit Checklist
The SOC 2 framework helps you identify potential risks to your business and mitigate them with approved controls. To pass a SOC 2 audit, you must first define your audit objectives, determine your audit scope, and undergo a number of preparation steps and assessments. While these steps can be time-consuming, expensive, and arduous, achieving SOC 2 compliance can have huge business benefits for organizations, from improved compliance risk management to more sales opportunities.
Best Practices for Responding to a GRC Vendor Assessment
Answering a GRC (Governance, Risk, and Compliance) vendor assessment is an important step for companies that want to demonstrate their commitment to compliance and risk management to potential customers. In this piece, we’ll cover how you can best respond to a prospect’s vendor assessment so you both can seal the deal. By following these best practices, you’ll be able to provide a comprehensive and accurate response to the assessment and establish a positive working relationship.
TrustCloud Onboarding
Vanta has joined the AWS ISV Accelerate Program
Today I’m excited to share the latest milestone in our growing partner ecosystem: Vanta has joined the Amazon Web Services (AWS) Independent Software Vendor (ISV) Accelerate Program. The AWS ISV Accelerate Program is a co-sell program for AWS Partners who provide software solutions that run on or integrate with AWS. Vanta’s acceptance into the program enables us to work in close collaboration with the AWS sales team to meet customer needs and provide better outcomes.