Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
August 2021
Bolster OT Security with Graylog
Anyone tracking the evolution of the IT industry is probably familiar with the concept of Industry 4.0. Essentially, it describes the process by which traditional industrial tasks become both digitized and continually managed in an IT-like fashion via modern technologies like cloud computing, digital twins, Internet of Things (IoT) sensorization, and artificial intelligence/machine learning.
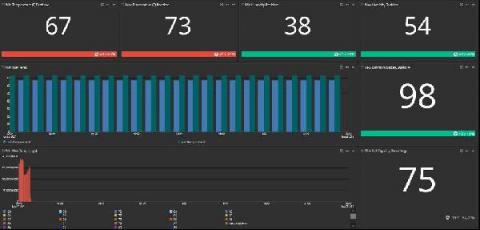
Metric Alerts
Docker Compose on Raspberry Pi4
What's New In 4.1
Endace and Kemp Technologies Partner to Provide Security and Network Teams with Deep Network Visibility
How to detect security threats in your systems' Linux processes
Almost all tasks within a Linux system, whether it’s an application, system daemon, or certain types of user activity, are executed by one or more processes . This means that monitoring processes is key to detecting potentially malicious activity in your systems, such as the creation of unexpected web shells or other utilities.
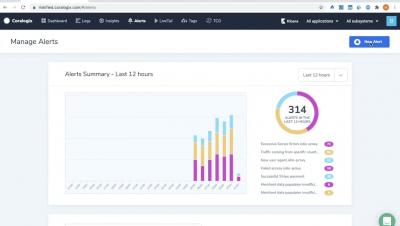
Detect security threats with anomaly detection rules
Securing your environment requires being able to quickly detect abnormal activity that could represent a threat. But today’s modern cloud infrastructure is large, complex, and can generate vast volumes of logs. This makes it difficult to determine what activity is normal and harder to identify anomalous behavior. Now, in addition to threshold and new term –based Threat Detection Rules , Datadog Security Monitoring provides the ability to create anomaly
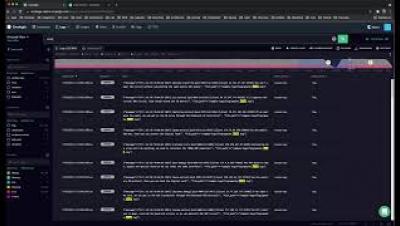
Graylog Logview
Canary Deployment: What you need to know
Canary deployment is a risk mitigation strategy for software releases. it allows applications developers to limit the damage caused by the release of faulty software updates and roll back such faulty updates quickly and safely without compromising the entire software assets.
Website security test: how to protect your business
Detectify expands coverage for public APIs (in development)
Credit Card Fraud Detection: Keeping Payments Safe with Machine Learning
Imagine, it’s a Saturday morning and you receive a call from a bank: – Hello? – Hi [insert your name], we suspect that a fraudster is trying to use your card at a grocery store in Texas. – Well, I am at a grocery store in Texas! – Oh my gosh! Do you see him? If only credit card fraud was funny.
Limitless XDR defined: Ingest, retain, and analyze security data freely
Elastic Security's newest features define the potential of XDR for cybersecurity teams. Our single platform brings together SIEM and endpoint security, allowing users to ingest and retain large volumes of data from diverse sources, store and search data for longer, and augment threat hunting with detections and machine learning. Security vendors are using the term “XDR” with increasing frequency, applying varied definitions to suit their respective technologies.
Elastic 7.14.0 introduces the industry's first free and open Limitless XDR
We are pleased to announce the general availability (GA) of Elastic 7.14, including our Elastic Enterprise Search, Observability, and Security solutions, which are built into the Elastic Stack — Elasticsearch and Kibana. Elastic 7.14 empowers organizations with the first free and open Limitless XDR, which delivers unified SIEM and endpoint security capabilities in one platform.
Detectify developing API security testing with fuzzing
Taking a Look at AWS and Cloud Security Monitoring
More and more companies understand the benefits of cloud computing, which is making their migration to the cloud more rapid. Per IDG’s 2020 Cloud Computing Study, 81% of organizations said that they’ve migrated either one application or a portion of their infrastructure to the cloud. The reasons why a company would shift its services towards the cloud depend on its business priorities, of course.