Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
opsdemon
Latest posts
The Results Are In: Cybersecurity Automation Is Crucial
Cybersecurity automation is no longer a “nice-to-have” — it’s a necessary component for security teams. The latest data reveals that organizations are increasingly recognizing the critical role automation plays in safeguarding their systems and enabling their teams to thrive. Here are the key insights.
The Economics of XDR: Reducing Costs and Enhancing Efficiency
As cyber threats get trickier—with ransomware attacks happening every 11 seconds, and each attack costing between $350,000 and $1.4 million on average—businesses want to beef up their defenses without spending too much. More companies are using Extended Detection and Response (XDR) to simplify their security work and cut costs. XDR provides an answer that can help businesses do more with less tackling common problems like too many tools complex security setups, and high running costs.
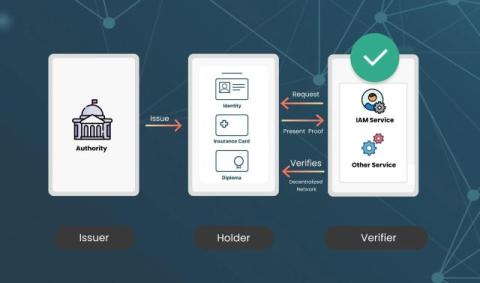
How Self-Sovereign Identity Will Transform User Verification in 2025?
Self-Sovereign Identity (SSI) is the latest privacy and security model that uses blockchain and cryptography to put you in control of your own identity. In this blog, we will dive into what SSI is all about, its core principles, real-life uses, and why it is set to transform how we manage identities in todays digital world.
Enforce Policies for IoT/OT Devices with Cato SASE
Managing firewall rules for IoT/OT devices can be complex—but not with Cato Networks. This video demonstrates how to create precise access rules for IoT/OT devices, like blocking Siemens PLC devices, using Cato's flexible, native SASE platform capabilities. Learn how Cato ensures secure, seamless operations. Visit our website for more info!
Arctic Wolf Labs Observes Threat Campaign Targeting Cleo MFT Products - Remediation Guidance
Update: Dec 11, 2024. Find the latest information in our follow-up security bulletin. On December 7, 2024, Arctic Wolf began observing a novel campaign exploiting Cleo Managed File Transfer (MFT) products across several customer environments. Initial indications of malicious activity in this campaign were identified as early as October 19, with a sharp increase in early December.
The Future of CMMC Compliance
Since its initial release in January 2020, the Cybersecurity Maturity Model Certification (CMMC) has undergone a series of fundamental changes. Fortunately, CMMC compliance requirements became much clearer when the US Department of Defense (DoD) published its CMMC Final Rule in October 2024. As a result, CMMC will have an impact on nearly every DoD contractor and subcontractor, and it’s anticipated that references to CMMC will be included in DoD contracts as early as March 2025.
Have I Been Pwned? 8 Ways to Protect Your Emails
Are you worried that your email has become one of over 14 million in a data breach? Then worry no longer! This article will give you all the advice to secure your email account, prevent your email from being leaked online, and minimize the risks of phishing, ransomware, and other cyber threats. The first step you will need to take in a have I been pwned situation is to check if your email has been exposed in a data breach.
See Falcon Foundry in Action
With cybersecurity tool sprawl on the rise, CrowdStrike Falcon Foundry allows you to easily build custom applications that operate as an extension of the CrowdStrike Falcon platform, allowing your team to consolidate dozens of point products. With access to a low-code app development platform and the same CrowdStrike data and infrastructure, your team will be able to build custom apps to solve the toughest cybersecurity challenges and stop adversaries.
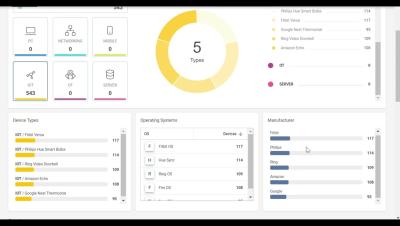
Extend IoT/OT Device Visibility in Cato SASE Cloud
Discover how Cato Networks revolutionizes IoT/OT security with its SASE Cloud platform. Watch this demo to see how we ensure seamless visibility, precise policy enforcement, and real-time threat prevention for your enterprise, all while simplifying security management and enhancing operational continuity.
Top Privacy Risks Startups Face and How to Mitigate Them
Startups often operate with limited resources, making them attractive targets for cybercriminals. According to Statista, the United States is home to some of the world's most successful startups, including Instagram, SpaceX, and Airbnb. While these companies have outgrown their startup phase, the region remains a vibrant hub for new ventures. Approximately 15% of the U.S. population is involved in startups.