Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
opsdemon
Latest posts
Simplify and Secure AWS Access to Accelerate Outcomes: 3 Best Practices
Companies may scale their cloud resources in pursuit of product, cost, or process innovation. However, this does not come without a cost of its own. The resulting infrastructure complexity, created from a growing sprawl of access silos, can introduce friction into engineer and security workflows.
The Real Cost of DevOps Backup Scripts
Backups can act as a safety net for DevOps. They help to keep important data safe and ensure smooth workflow and business resilience in the midst of a disaster. However, which backup method is the most efficient one? There are different options for backing up your DevOps stack which range from basic scripts put together by internal IT teams to advanced solutions provided by professional backup vendors.
How Calico Configuration Security Works
In today’s cloud-native ecosystems, effective configuration security is essential. Containers and Kubernetes clusters operate in dynamic environments with multiple interconnected risk vectors, making security more complex than in traditional IT environments. Misconfigurations can lead to vulnerabilities, breaches, and compliance issues, putting applications and data at risk.
Getting the Scope Right: The Foundation of CMMC Level 2 Certification
Why are we talking about scoping? For defense contractors, subcontractors, or suppliers, the surest path to CMMC Level 2 certification success depends heavily on an accurately defined CUI boundary, or “CMMC assessment scope”. The wait may be over, as the DoD has finalized its expectations of the CMMC program, but the lion’s share of defense contractors are just getting started, many with a heavier lift than others.
Understanding the EU Cyber Resilience Act: A New Era for Digital Product Security
Cyber resilience is a constant topic of concern in technology and cybersecurity, as it approaches security from the standpoint of assuming that attacks are inevitable rather than solely attempting to prevent them. Layered cybersecurity is crucial to ensure comprehensive defense against a wide range of threats.
8 Emerging Cybersecurity Scams And Their Implications For The Future
Technological advances usually lead to a brighter future. While that may be true, these developments could also be used to refine and increase cybersecurity scams. Attackers do not care about who they target as long as they get people's and establishments' information and credentials. Cybersecurity professionals must be aware of the current scams plaguing the digital world and how to combat them. Here are a few examples and their implications for the future.
Replacing Traditional Security Models: Why the Shift to Zero Trust Matters
The increasing sophistication of cyber attacks, the proliferation of cloud services, and the new normal of remote work have all changed the modern cybersecurity landscape. As traditional perimeter-based approaches to security become increasingly vulnerable to these modern cyber threats, zero trust has emerged as the modern security strategy of choice. Zero trust architecture is critical for any organization seeking to improve resilience, reduce breach risk, and enhance data protection.
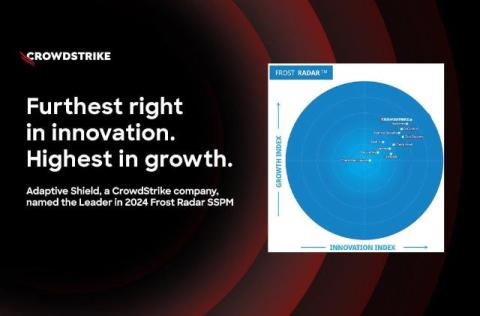
Adaptive Shield, a CrowdStrike Company, Leads in 2024 Frost Radar SSPM Leadership Report
CrowdStrike is proud to announce that Adaptive Shield is positioned as the leader in the Frost & Sullivan 2024 SaaS Security Posture Management (SSPM) Frost Radar, earning the highest and farthest-right position among all evaluated vendors. Adaptive Shield, which was acquired by CrowdStrike in November 2024, is recognized for its leadership in innovation and growth, with scores of 4.8/5 and 4.5/5, respectively, on the Frost Radar innovation index.
Kubernetes 1.32 - A Security Perspective
Kubernetes continues to evolve its security posture with version 1.32, introducing several significant improvements in authentication, authorization, and auditing mechanisms. These enhancements provide more granular control, improved traceability, and stronger security defaults.
How to Handle Secrets in CI/CD Pipelines
Securely managing secrets within the CI/CD environment is super important. Mishandling secrets can expose sensitive information, potentially leading to unauthorized access, data breaches, and compromised systems.