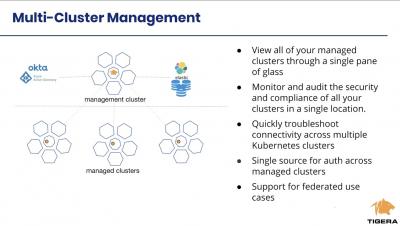
Before Covid-19, there were many reasons why employees worked remotely. For some, it was about removing distractions, and for others, it was about maintaining a healthy work-life balance. But as the world starts to reopen, companies now need to decide whether they continue to allow employees to work remotely or not. According to SHRM, 50% of companies recently surveyed, intend to keep offering a hybrid work arrangement, which means that organizations will need to find ways to monitor and manage employees while they’re in the office or at home. The benefits and challenges of a hybrid workforce Gauging employee productivity and engagement using technology How remote monitoring tools can provide metrics for companies of all sizes