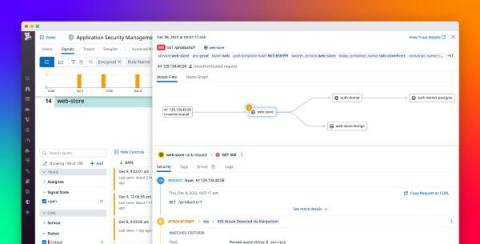
Secure serverless applications with Datadog ASM
The popularity of serverless architectures continues to grow as organizations seek ease of scalability and to eliminate the need to provision and manage infrastructure. In fact, in our most recent State of Serverless report, we found that more than half of our customers have adopted serverless technologies offered by Azure, Google Cloud, and AWS.