Supply Chain Cybersecurity: Ensuring the Security of the Digital Ecosystem
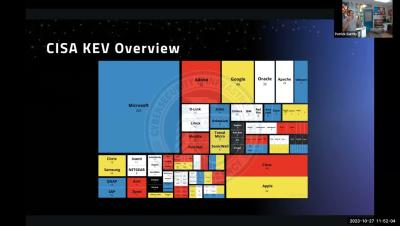
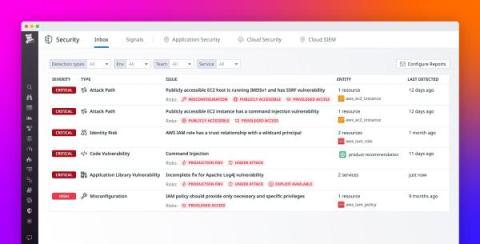
The digital ecosystem is an intricate web of interconnected technologies and processes. Within this network, supply chain cybersecurity has emerged as a critical component to safeguard against the growing threat landscape. As supply chains become increasingly digital, they also become more vulnerable to cyber attacks that can disrupt operations and compromise sensitive data.