Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
February 2023
6 Tips to select "RIGHT" Digital Risk Protection Vendor
In today's ever-changing digital world, users of digital risk protection solutions encounter various obstacles. Although the top players in the digital risk protection industry provide powerful solutions that come with an array of features and capabilities, customers must still navigate a complicated and fast-moving environment of potential threats.
A Breach Makes You Stronger
There are two kinds of CISOs: pre-breach and post-breach. Pre-breach CISOs are overly focused on tools and thinking about investing in prevention technologies. They do this almost to the exclusion of thinking about recovery and timely restoration of services once something bad actually occurs. And something bad will happen; it’s not a matter of if, but when (and how often, I might add, so “breach cadence” seems a more suitable KPI than breach likelihood).
Shifting to Business Ecosystem Risk Management
Third-party risk management is a well-known industry term that emphasizes the importance of looking outside yourself to identify potential risks to your organization. In the current business landscape, where you are communicating and collaborating with dozens, if not hundreds, of other organizations, focusing on your own cyber risk and that of your third parties is not enough.
Cybersecurity Insights from The World Economic Forum in Davos: Part II
On the final day of the World Economic Forum, we shared SecurityScorecard’s five key cybersecurity insights based on the discussions that dominated our time in Davos, Switzerland. Several weeks later, after gathering our thoughts from everything we saw, heard, and contributed to in Davos, we’d like to expand on our cybersecurity perspectives from the Forum and provide five additional insights.
I Am Suing You! Legal Threats in Phishing Emails
Unless you’ve been avoiding your inbox like a cybercriminal avoids sunlight, you’ve probably seen something like this before: That right there is a classic example of a phishing email. Most security-aware individuals can spot a phishing email from a mile away. In the past, it used to be the misspellings, such as in this email, that gave it away. Now, misspellings and poor grammar aren’t ideal indicators of phishing attempts.
2023 North America Security Trends: Staying Ahead of Modern-Day Risks
New Feature: NIST CSF Mitigation Recommendations
Oakland declares a state of emergency over ransomware attack
The city government of Oakland has declared a state of emergency after it was hit by a ransomware attack. The attack, which began in the evening of February 8th, has forced the city to take all its IT systems offline, and has affected many non-emergency services, including the ability to collect payments, issue permits, and process reports.
Gain visibility into open source vulnerabilities with Datadog Application Risk Management
Open source libraries have become an indispensable part of modern applications. Approximately 90% of organizations use open source software to support their services, but monitoring these dependencies can be difficult when environments run thousands of ephemeral services. The complex nature of modern applications, in combination with the challenge of keeping a competitive edge in a fast-moving market, can make it difficult for organizations to identify and remediate threats in a timely manner.
How to Measure Cyber Risks in Healthcare
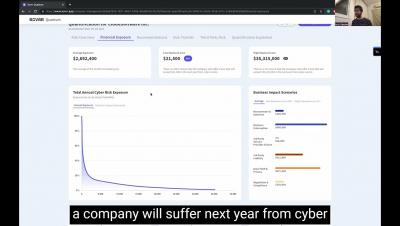
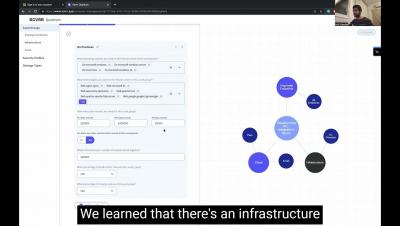
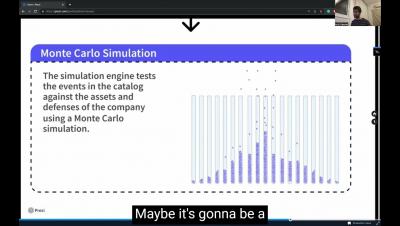
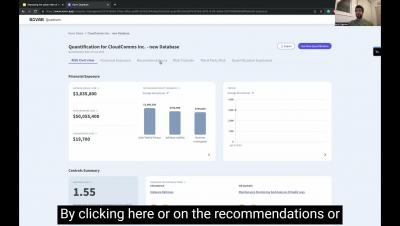
Cyber risks are prevalent in all healthcare institutions, and understanding how to mitigate those risks is especially important in today’s cyber landscape. Cyber risk is the sum of all IT risks that can potentially lead to the loss or exposure of critical data, financial damages, reputational damages, and operational stoppages due to a data breach or data leak. Measuring cyber risks involves determining the likelihood and impact of each cyber threat.
Info-Stealers Are on the Rise: A Look into Stealerium
Info-stealers are malicious software designed to extract sensitive information, such as passwords, from victim systems. Info-stealers have become one of the most discussed malware types in cybercriminal underground forums. Let’s see how info-stealers have evolved recently to become the threat that they are. Then, we’ll look at a specific stealer freely available as open-source that could be used in future attacks.
January Cyber Roundup
Importance of Insurance-Validated Risk Models to Quantify Cyber Risk
2022 seems to be on target for the lowest year of reported breaches by large US corporations
Why Hackers Love Credentials: Parsing Verizon's 2022 Breach Report
Cybersecurity Risk Management: 5 Steps for Assessing Risk
SecurityScorecard releases list of Killnet open proxy IP addresses
In the wake of Killnet’s latest DDoS attack on U.S. hospitals on January 30, SecurityScorecard has made its KillNet open proxy IP blocklist available to the public. This list is the product of the SecurityScorecard Threat Research, Intelligence, Knowledge, and Engagement (STRIKE) Team’s ongoingresearchintoKillNet. We released this list to help organizations better defend themselves against KillNet and other groupslike it by preventing traffic from exploitable assets.
Ask A Ciso Series: Part 3 - How should CISOs prepare themselves for 2023 challenges?
Revolutionize risk: How to manage risk with Vanta
Killnet: A new group exploiting an old problem
How geopolitics and hacktivism is causing trouble for the healthcare industry
Close Encounters of the Third- (and Fourth-) Party Kind: The Blog
With organizations becoming increasingly digitally connected, a lack of visibility into their vendors’ security diligence has made exploiting these relationships a go-to tactic for cybercriminals. So, what can organizations do to minimize risk stemming from their business ecosystems?