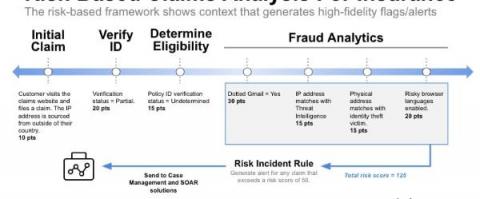
Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
November 2022
9 Steps to Mitigate Ransomware Attacks for Your Business
Ransomware attacks have become so prevalent in recent years that it’s no longer a matter of “if” your business may be the victim of a ransomware attack, but “when.” In fact, in 2021, 37% of global organizations reported that they were the victim of a ransomware attack. To mitigate the impact and probability of ransomware on your business, you must continuously look for new ways to secure your network and maintain continuous cybersecurity monitoring.
UpGuard Creating Risk Waivers in Risk Assessment Demo // Chris Schubert, Senior Product Manager
UpGuard Known Exploited Vulnerabilities (KEV) Demo // Annie Luu, Product Marketing Manager
UpGuard Shared Profiles and NDA Protection // Harsh Budholiya, Product Marketing Lead
UpGuard Product Spotlight // Dan Bradbury, Chief Product Officer
Up Level Your Amazon Security Lake with Attack Surface Intelligence
As global network infrastructure expands to include devices without traditional compute power, every organization’s attack surface becomes increasingly complex. Parallel to the increased complexity in the threat landscape is the increased scale and complexity of the signals and data necessary to produce meaningful cybersecurity insights. At its core, cybersecurity is a big data problem, requiring centralization of disparate data sources in uniform structure to enable continuous analytics.
Ransomware Attacks and Remediation Strategies for Financial Institutions
Believe it or not, the Financial Services industry has one of the slowest vulnerability remediation rates, with a median of 426 days. “Financial regulators can no longer rely on static, point-in-time assessments to understand the cybersecurity risks posed to the financial system,” said Sachin Bansal, SecurityScorecard’s Chief Business and Legal Officer, in a recent BusinessWire article. “Continuous monitoring tools must be a part of every regulator's toolbox.”
Leonardo UK selects Rizikon from Crossword Cybersecurity to assist with assessment of supply chain cyber risks
How to choose a CRQ framework
To get a handle on increased cybersecurity threats, businesses need to know what’s at stake. If you don’t know what you’re defending and what the implications of a cyber event could be, then it’s hard to make cybersecurity decisions. For example, you could be spending time and money on cybersecurity awareness training while your biggest vulnerabilities stem from third-party exposure.
Framing the Modern Conversation Around Digital Transformation and Digital Risk
Following my recent AISA session about security transformation in October, I am digging further into the value that can come from both security and digital transformation, applying security service edge capabilities and zero trust principles as part of the broader digital transformation strategy.. In the first part of this three-part blog series, I am going to take a look at how an understanding of digital strategy and digital risk are foundational to a modern security transformation journey.
Mobile Device Forensics: Challenges, Threats, & Solutions
Mobile forensics is the process of accessing, recovering, and analyzing digital evidence from mobile devices using a court accepted methodology. The information that can be gleaned from a criminal’s phone is highly valuable. That’s why mobile forensics and digital forensics as a whole are valuable assets for law enforcement and intelligence agencies worldwide.
3 Key Trends in Today's It Security Landscape
Diagnosing Board Reporting and Its Challenges
Three-quarters of U.S. CEOs in PwC’s 24th Annual Global CEO Survey said they are “extremely concerned” about cyber threats. They want to understand roadblocks, cyber insurance coverages, and budget allocation, among other critical topics. CISOs prefer the language of technology, and boards prefer the language of finance.
Russian-Speaking Threat Actors Claim New DDoS Attacks Against U.S. Targets
Citing senior Cybersecurity and Infrastructure Security Agency (CISA) officials, journalistsreported on November 8 that DDoS attacks had temporarily disabled the website of a state government. A group claiming to be pro-Russian hacktivists, CyberArmyofRussia_Reborn, claimed responsibility for that attack and another on the website of a U.S. political party’s governing body on the same day, specifying one target IP address for each organization.
Reputational Risk Mitigation
Simplify your procurement process and subscribe to Splunk Cloud via the AWS marketplace Unlock the secrets of machine data with our new guide All companies want to protect their reputation as any mishandling of it, either self-inflicted or via outside forces, can have a devastating impact. Mitigating reputational issues involves mitigating the risk that leads to them.
The Future of Digital Forensics: Challenges & Opportunities
With the rise in cybercrime, including malware and ransomware attacks, digital forensics has become vital for many organizations. Digital forensics is the science of recovering, investigating, and analyzing digital records, often called digital artifacts, or in legal language forensic artifacts. This can be to find evidence of a crime, but is more often used to identify activity occurring on a computer and to understand how a cyberattack or breach may have occurred.
SecurityScorecard Enables Cyber Insurers to Shift from Static to Dynamic Loss Control
It’s no secret that loss control programs are essential for cyber insurance. Unlike other forms of insurance where the risk and assets don’t change much during a policy term, cyber insurance is meant to mitigate a constantly evolving risk and cover organizations whose security posture is always changing. A cyber insurance policy could be priced completely differently today compared to a few weeks or months later.
How Patching Thwarts Cyber Attackers
FTX, risk management, and attack surfaces - Visibility is the Key
The FTX crypto disaster is a great lesson in risk management. It brings into focus the importance of knowing where your valuables are and how they are being managed.
Crossword's Trillion protects Spanish Public Administration against threat of digital identity and credentials misuse
New Features: Third Party Cyber Risk Quantification & Data Transparency
Third party cyber risk can be a lot like the wild wild west - it’s hard to predict where your next loss will come from. We know that third-party cyber events can lead to millions of dollars of loss revenue, remediation costs, regulatory fines & more. That’s why Kovrr has made significant updates to their platform to help put a financial quantification on risk derived from your organization’s third parties.
How to Improve CISO & Board Member Communication
What's the Difference Between Red Teaming and Penetration Testing?
When discussing cybersecurity, “penetration testing” and “red teaming” are two terms that are often used interchangeably but are two entirely separate concepts. If you are considering implementing additional cybersecurity protocols within your organization, it’s essential to understand the unique role and function of each of these processes and how they can benefit your organization.
SecurityScorecard Provides Comments to FERC's Proposed Risk-Based Cybersecurity Rulemaking
SecurityScorecard, the global leader in cybersecurity ratings, commented on the Federal Energy Regulatory Commission’s (FERC or “Commission”) proposal to establish rules for incentive-based rate treatments for certain voluntary cybersecurity investments by utilities. Cybersecurity is among the greatest threats to the resilience and reliability of America’s critical infrastructure, including its electricity infrastructure.
Key Cybersecurity Trends in 2023
Why is a cybersecurity risk assessment necessary?
The cybersecurity landscape is constantly evolving. Criminals are always searching for new ways to compromise enterprise systems, looking for weaknesses in their security.
What's new in UpGuard // Cyber Vendor Risk Management Product Releases
KillNet Operations Against U.S. Targets Persist With Attempted Airport Website Attacks
In October, BleepingComputer reported that the websites of several airports were experiencing service disruptions after the KillNet threat actor group announced that they would target airports throughout the U.S.
Build an Agile Security Program and Power Actionable Insights with Confident Data
In today’s rapidly evolving cyber risk landscape, a resilient and trusted digital ecosystem is possible with an agile security program. Cyber resiliency is the ability to respond to and recover from a cybersecurity incident effectively. A record high 71% of organizations were victimized by a ransomware attack in 2022. Even more concerning is that Gartner estimates that 80% of organizations have no knowledge or awareness of their attack surface.