Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
September 2023
Qualitative vs. Quantitative Cybersecurity Risk Assessment
Risk mitigation is at the heart of cybersecurity. By connecting to the Internet, implementing upgraded IT systems, or adding a new vendor to your organization, you are automatically exposing your business to some level of cyber risk. With outsourcing on the rise and a growing reliance on vendors who are processing, storing, and transmitting sensitive data, assessing and mitigating risk is becoming increasingly important.
Overcoming Cybersecurity Headwinds Part 2: Automation and Repurposing Time Savings
Combining IT and OT security for enhanced cyber risk management
Historically, IT and OT have operated in separate worlds, each with distinct goals and protocols. IT, shaped by the digital age, has always emphasized the protection of data integrity and confidentiality. In this space, a data breach can lead to significant consequences, making it crucial to strengthen digital defenses. On the other hand, OT, a legacy of the Industrial Revolution, is all about ensuring machinery and processes run without interruptions.
How we operationalize security risk assessments at Vanta
This post is part of an ongoing series where you’ll hear directly from Vanta’s own Security, Enterprise Engineering, and Privacy, Risk, & Compliance Teams to learn about the team’s approach to keeping Vanta—and most importantly, our customers—secure. In today’s post, you’ll hear from Rob Picard, who leads Vanta’s Security team, and Matt Cooper, who leads Vanta’s Privacy, Risk, & Compliance team.
Over 53% of Organizations Have An Internet-Exposed Vulnerability
GDPR Compliance Guide: A 9-Step Checklist
With many nuances to consider, adhering to the General Data Protection Regulation (GDPR) requirements can be a daunting task. After all, the entirety of the GDPR consists of a whopping 99 Articles. Fortunately, by following a GDPR security checklist, you can help your organization ensure that all required facets of data security are covered without sifting through pages and pages of legalese.
A Deep Dive into the Exploit Prediction Scoring System EPSS
5 Strategies to Reduce Attack Surface Exposure
Just How Accurate Are Security Ratings?
Third-party cyber risk is now one of the biggest threats today, according to many CISOs. Security leaders point to the fact that many of the recent major breaches have been a result of a single software supply chain vulnerability: SolarWinds, Log4j, and MOVEit, just to name a few.
Effective Cybersecurity and Risk Management Starts Here
BlueVoyant Digital Risk Protection
Unpacking ISO 31010: Effective Risk Assessment Techniques
How to Prevent Third-Party Vendor Data Breaches
SmokeLoader's Plugins
Power Up with AI - How to Take Your GRC to the Next Level
Why Does Cyber Insurance Exists?
What is the Cost of Cyber Liability Insurance?
In today’s digital age, where businesses rely heavily on technology and data, the risk of cyberattacks and data breaches has become a constant concern. These incidents can lead to significant financial losses, damage to a company’s reputation, and even legal liabilities. To mitigate these risks, many businesses turn to cyber liability insurance. But what exactly is the cost of cyber liability insurance, and how do insurers determine it?
5 Risks Of Outdated Software & Operating Systems
What is Cyber Attack Insurance?
Businesses of all sizes are increasingly reliant on technology to conduct their operations efficiently. While technology offers numerous benefits, it also exposes organizations to a growing threat—cyber attacks (or cyberattacks). As the frequency and sophistication of cyber threats continue to rise, businesses are turning to a crucial safeguard: cyber attack insurance.
MOVEit Transfer: Detecting affected servers at scale
Don't Reuse Passwords Or Else This Can Happen
Why we need to democratize governance, risk, and compliance
Today’s uncertain economy has presented an array of problems to organizations of every size and across all industries. In the world of tech titans alone, 70,000 jobs have been lost over the past year. It’s safe to say that businesses have laid off and lost talented and experienced professionals from their rosters. We feel losing talent more acutely in cybersecurity and privacy as risk of cyberattacks and breaches may cost the global economy $10.5 trillion annually by 2025.
What is Calculated Risk in Business?
Cloud Threats Memo: Mitigating the Risk of Third-party Apps
The use of third-party apps (also known as “connected apps”, “cloud to cloud apps”, “OAuth apps”) are apps developed by external and internal developers or organizations that can interact with and extend the functionality of a primary SaaS App. These are growing exponentially across organizations.
5 Steps to Performing a Cybersecurity Risk Assessment
What is ISO 31000? An Effective Risk Management Strategy
The Top 7 Cyberattacks on U.S. Government
In a world where ones and zeros are the new battleground, these threats, cyberattacks have become a significant threat to governments worldwide. The United States, with its vast array of government agencies and critical infrastructure, is no exception. Cybersecurity threats that impact the public sector range from state-sponsored attacks to financially motivated hacking groups. In this blog post, we’ll delve into the top 7 cyberattacks on the U.S.
3 Tangible Benefits of an A Rating
Security ratings are a standard in cybersecurity. Many organizations rely on them to manage their security programs and they create ROI for the organization. Despite the potential benefits, it can be challenging for organizations who are evaluating different security ratings options to determine the value they will get from them. When making investment decisions, it’s essential to know where the investment will take you and quantify that benefit.
Overcoming Cybersecurity Headwinds Part 1: Start With a Unified Approach
Cyber Risk Exposure: How to Act When You Can't Measure Risk
UpGuard Summit September 2023 - Panel Discussion
Take advantage of our helpful Third-Party Risk Management Services
Kickstart your risk assessment process with the improved risk assessment tool
Discover UpGuard's responsible use of generative AI and Large Language Models
UpGuard Product Spotlight Q3 2023
Why Reduce Software Supply Chain Risks with Intelligent Software Security
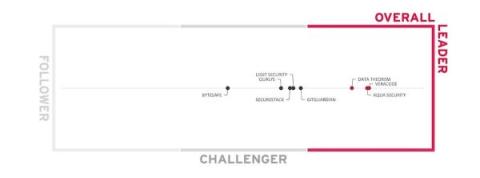
There’s a growing array of risks lurking within the supply chain of the digital solutions we increasingly depend upon. Leaving gaps in your software supply chain security (SSCS) could spell disaster for your organization. Let’s explore how new analysis defines an end-to-end solution and why Veracode was ranked as an Overall Leader, Product Leader, Innovation Leader, and Market Leader in the Software Supply Chain Security Leadership Compass 2023 by KuppingerCole Analysts AG.
Using a Standardized Approach for Measuring Cybersecurity in Government
Last week at the annual Billington CyberSecurity Summit in Washington, DC, officials from government agencies gathered with industry leaders to discuss cyber threats, as well as geopolitics and issues of national security. One of the highlights was a fireside chat on Friday with Anne Neuberger, deputy national security adviser for cyber and emerging technology.