Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
October 2023
How Security Ratings Can Harmonize Cybersecurity Regulations
In July of this year, the Office of the National Cyber Director (ONCD) stated in its release of an RFI on regulatory harmonization that: “When cybersecurity regulations of the same underlying technology are inconsistent or contradictory—or where they are duplicative but enforced differently by different regulators … consumers pay more, and our national security suffers.” This is an understatement. SecurityScorecard agrees and was happy to share our comments with ONCD today.
Cyber Trust and Transparency
In cybersecurity, the terms “trust” and “transparency” are often mentioned. And while they should no doubt be a priority, they can also be difficult to quantify. Good CISOs recognize that transparency in cybersecurity isn’t a one-time effort. It’s a continuous process that involves a near-constant state of evolution. But with the right tools and systems in place, it’s possible to not only measure trust and transparency but improve them as well.
Identifying Assets for IT Risk Analysis
What's new in Riscosity: October
Custom Descriptions Teams can now design custom descriptions to provide context as to why a finding was ignored, resolved or marked as false positive. Previously, teams were provided a set of out of the box options, for the common use cases. The new flow resembles a standard documentation process where canned and contextual responses are available to help scale internal communication.
Effective Workflow For Your Audit Management Process
Top 3 Vendor Cybersecurity IT Risk Assessment Templates
SEC's Cybersecurity Regulations, Part III: The Relationship Between the CISO & The Board
Key Steps to Improving Strategic Vendor Management
The Benefits of Using a Compliance-Oriented Data Management Platform
The Evolution of the CISO
CISOs and security leaders are constantly being reminded that cyber risk is now a business risk. And at the same time, organizations are realizing the financial implications of not having cyber expertise on their boards.
How to Resolve SSL Configuration Risks
Cyberint Named as Frost & Sullivan's 'Company of the Year' in the Global External Risk Mitigation and Management Industry
Industrial Control Systems are Exposed: Breaking Down the Risks
SIG Lite Questionnaire
A Deep Dive Into Cloud Security Assessments
Cloud platforms offer unparalleled scalability, flexibility, and cost-efficiency. However, the convenience and advantages of the cloud are accompanied by significant security challenges. Hackers are constantly trying to exploit weak cloud configuration settings, which is why it’s important to have visibility into the security of your organization’s cloud infrastructure.
Free Template: Vendor Post-Data Breach Questionnaire (2023)
Third-Party Security Risks: How to Mitigate Potential Cybersecurity Threats
How to Conduct an ISO 27001 Risk Assessment
Welcome to our comprehensive guide on ‘Conducting an ISO 27001 Risk Assessment’. This blog is designed to equip you with effective strategies for a successful risk assessment, incorporating the principles of ISO 31000 risk management. Risk assessment is a vital component of a robust information security framework and is in alignment with ISO 31000.
Preparing for a Cyber Catastrophe With a Data-Driven Risk Appetite
Introducing UpGuard's New SIG Lite Questionnaire
What is the Probability of a Data Breach?
Cybercrime is on the rise. By 2025, the cost of cybercrime around the world is estimated to escalate to $10.5 trillion, based on a year-over-year increase of 15%. This number represents the potential for the largest transfer of economic wealth in history and exceeds even the total global profits from the illegal drug trade.
Secure Third-Party Connections
Riscosity has joined forces with SecurityScorecard! This new partnership enables SecurityScorecard and Riscosity users to scale their business using only trusted vendors and ensuring that the right data is going to the right place. Together we’re helping compliance and security teams scale their programs, and significantly reduce their applications' attack surface.
Navigating the Challenges of Enterprise Vulnerability Management
The Federal Risk and Authorization Management Program (FedRAMP) FAQ
FedRAMP, which stands for Federal Risk and Authorization Management Program, is a U.S. government-wide program that standardizes the security assessment, authorization, and continuous monitoring processes for cloud products and services used by federal agencies. The goal of FedRAMP is to ensure the security of cloud-based systems and protect sensitive government data. Key objectives of FedRAMP include.
Why every security team needs to be prepared for the unexpected
The traditional enterprise risk model is a thing of the past. Cybersecurity risk cascades into almost every part of an organization, triggering legal fallout, technology risk, compliance issues, and more. Bottom line, third-party cyber risk is a material business risk. A recent report found that 80% of organizations experienced at least one data breach caused by a third party last year.
SecurityScorecard Achieves FedRAMP 'Ready' Designation
SecurityScorecard is proud to announce that it has achieved the Ready Designation under the Federal Risk and Authorization Management Program (FedRAMP). This designation demonstrates SecurityScorecard’s commitment to the rigorous security standards required by the U.S. government for cloud service providers, and it will enable the company to meet growing demand from U.S. federal agencies for its Third-Party Cyber Risk Management Platform. U.S.
SecurityScorecard Research Investigates Chinese Threat Actor Group
In late August, Microsoft published its analysis of espionage activity tied to a new threat actor group called Flax Typhoon, which is believed to operate on behalf of the People’s Republic of China (PRC). The group mainly targets Taiwanese critical infrastructure, including: government, education, manufacturing, and information technology sectors.
Vendor Offboarding: Best Practices for Ensuring Security
CISA KEV's Known Ransomware Attribution
A Deep Dive Into Security Testing
With the average cost of a data breach now at $4.35 million, it’s time for organizations to take proactive measures to protect themselves against cyber threats. By conducting thorough security testing, organizations can gain a deeper understanding of their security posture and make informed decisions about where to allocate their resources to improve their overall cybersecurity readiness.
Evolution of Cybersecurity: From Passwords to On-Demand CRQ
What's new in UpGuard // Cyber Vendor Risk Management Product Releases
Board Members' Guide to Cyber Governance and Leadership
Last week, I had the opportunity to moderate a panel at the NACD Summit, where I was joined by: Deven Sharma, Former President at S&P; John Katko, Former Member of U.S. House of Representatives; and Aaron Hughes, CISO at Albertsons. The National Association of Corporate Directors (NACD) holds its summit annually to empower directors and transform boards to be future ready. Our panel discussion focused on how board members can strategically oversee their organizations’ cybersecurity resilience.
Release Spotlight: Trends Page Upgrade and Bulk Data Export Functionality
Re-evaluating risk in the artificial intelligence age
It is common knowledge that when it comes to cybersecurity, there is no one-size-fits all definition of risk, nor is there a place for static plans. New technologies are created, new vulnerabilities discovered, and more attackers appear on the horizon. Most recently the appearance of advanced language models such as ChatGPT have taken this concept and turned the dial up to eleven.
The IR Retainer Redefined: Boosting Cyber Resilience with MDR + Cyber Risk Retainer
An effective detection and response capability is essential for monitoring key assets, containing threats early and eradicating them. However, due to the current disparate nature of potential attack vectors within an organization, affording the wide range of sensors necessary can be a challenge as well as the worry of the disruption of critical services. Yet, without robust detection and response processes, businesses are left vulnerable.
Navigating the Unknown: Zero-Days in the Supply Chain
Zero-days are out there. Lurking just under the surface, waiting for the right moment to strike. A security team can do everything right and still experience a zero-day attack in its supply chain. And with innumerable configurations, devices, and platforms that can be exploited, zero-day exploits are becoming more common than ever.
Mastering Cybersecurity in Today's World
In a world where AI is everywhere, cybersecurity regulations are on the rise, and cyber insurance is booming, we need standardized metrics for cybersecurity. Remember, you can’t manage what you can’t measure. A recent report by SecurityScorecard and the Cyentia Institute discovered a startling fact: 98% of organizations have a third party with a breach in the last two years. In cybersecurity, metrics matter; knowing how to communicate and report on metrics is essential.
CISA KEV Ransomware Interactive Visualization
What Is Security Posture?
10 Frequently Asked Supplier Risk Management Questions
What is Threat Exposure Management?
Staying ahead of cyberattacks and strengthening your organization’s defenses doesn’t happen overnight and can be hard to accomplish without the right tools and cyber strategies. SecurityScorecard’s Threat Intelligence team hosted a webinar that highlights the importance of threat exposure management, its latest trends, and how to implement this framework into an organization’s cybersecurity plan.
Your Sender Policy Framework (SPF) Risk Exposure
How a Database Risk Assessment Reduces the Risk of a Cyberattack
Database security often, and to an organization's detriment, falls between the cracks as security and IT teams scramble to stay on top of daily cyber hygiene tasks and deal with the never-ending problems of running their network. The danger of overlooking their database, or to put it in, say, banking terms – the vault – is this is likely a threat actor's primary target. An organization's database is where IP, credentials, and financial information are stored.
Understanding Insurance Risk
BlueVoyant Comprehensive Supply Chain Defense
Vendor Due Diligence Checklist: 5 Steps to Selecting a Third-Party
Why a robust risk management and cyber resiliency plan is an absolute necessity
As we are in the midst of Cybersecurity Awareness Month, and in the lead-up to our own Secure Connected Future Summit which we are hosting in November, I feel that a lot of the focus when it comes to cybersecurity still tends to be on prevention tactics. However, I would argue that it is not just about having the right defensive cybersecurity tools in place, but it is also about understanding how the organisation will recover from an incident – how quickly and at what cost to the business.
SecurityScorecard Cybersecurity Data Incorporated into S&P Global Market Intelligence's Newly Launched Supplier Risk Indicator
The world around us is often a reflection of who we are and what we value. The same can be said for businesses. It’s no longer enough to be resilient, trustworthy, and secure your own organization; the companies you do business with need to meet these same standards.
Creating a Vendor Risk Summary Cybersecurity Report in 2023
Creating a Cybersecurity Report for Senior Management in 2023
New from SEC: Cybersecurity Final Rule on Reporting Hits Third Party Risk
Kovrr Highlighted in Gartner's CRQ Category in Gartner Hype Cycle
Securing Our World
October is Cybersecurity Awareness Month, a dedicated month for the public and private sectors to work together to raise awareness about the importance of cybersecurity. And this year’s theme, “Secure Our World,” couldn’t be more timely. With the growing number of cyberattacks worldwide, it’s becoming increasingly apparent that critical infrastructure is at risk.
What is a Zero-Day (0-Day)?
In the world of cybersecurity, zero-day vulnerabilities, zero-day attacks, and zero-day exploits keep many CISOs up at night. These terms, often shrouded in mystery and intrigue, denote a significant risk to digital systems and the sensitive data they hold. Understanding the intricacies of zero-day vulnerabilities and the exploits that leverage them is crucial for individuals, organizations, and governments seeking to fortify their defenses against cyber threats.
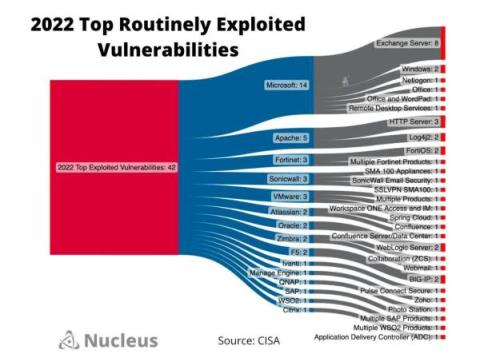
A Look at CISA's Top Routinely Exploited Vulnerabilities
Boost your business with cybersecurity risk assessments
The factors that pose risks to companies are constantly changing. Clinging to a single defense strategy can be counterproductive, as this strategy can quickly become outdated and ineffective. As a managed service provider (MSP), you may have found that your customers are unwilling to consider new cybersecurity tools unless there is a problem, or they aren’t satisfied with their existing solution.
Building a Cyber-Resilient Future Together
Last week in New York, I had the opportunity to attend a panel discussion hosted by SINET and moderated by Upendra Mardikar, the Chief Information Security Officer of TIAA. We discussed everything from security in DevOps, to AI’s pros and cons, and cybersecurity’s future. As long as the attack surface, API usage, and digital footprints increase, so will cyber risk.
Improvements to Detecting Modern Financial Crime
The Future of Cybersecurity: ChatGPT For Risk Management?
Medical Device Security Risk Assessment [Download XLS Template]
When you think about hacking stuff, you probably don’t consider thermometers and pacemakers. But imagine the implications if that chunk of metal inside your body suddenly starts acting weird. From the humble thermometer to the sophisticated MRI machine, these gadgets are vital cogs in the healthcare machine and potential Trojan horses if not correctly secured.
New Gartner Forecast Shows Global Security and Risk Management Spending to Increase by 14% in 2024
Gartner issued a press release that forecasted global security and risk management end-user spending to reach $188.1 billion, along with worldwide end-user spending on security and risk management projected to be $215 billion in 2024.
What is Vulnerability Remediation?
Due to the increasing frequency and impact of cybersecurity threats, vulnerability management has become a heightened priority for many organizations. While businesses often focus on vulnerability assessments when developing their vulnerability management programs, assessments are only the first step in a holistic cybersecurity threat mitigation strategy. One aspect of vulnerability management that is often overlooked is vulnerability remediation.
Nurturing a Resilient Security Culture: An Insider's Perspective
Overcoming Cybersecurity Headwinds Part 3: Future Proofing Your TPRM Program
The role of automation in mitigating cybersecurity risks
Cyberattacks are on the rise around the globe. Recent data suggest that there are 2,200 cyberattacks every day and that the average cost of a data breach is $9.44 million. Of those cyberattacks, 92% are delivered via email in the form of malware and phishing. In 2022 alone, businesses reported 255 million phishing attacks with an average cost of $4.91 million.
Advancing Digital Resilience in the Financial Sector
Financial entities throughout the European Union are preparing for the Digital Operational Resilience Act (DORA), a new piece of legislation to strengthen the digital resilience of credit institutions, investment firms, insurers, and more. DORA focuses on breach prevention and cyber resilience, meaning financial institutions must prioritize both protecting their attack surface and incident response planning.
SEC Regulations: What is a "Material" Cybersecurity Incident?
What CIS Controls are Effective for Successful Cyber Defense?
Critical Security Controls are a set of cybersecurity principles and actions that list defense tactics and best practices to mitigate against popular cyber-attack methods. But what makes them so valuable is that the framework prioritizes a small number of actions that all work to significantly reduce cybersecurity risk across your network. Keep reading to learn more about CIS controls, as well as which controls are essential for successful cyber defense.
Bitsight identifies nearly 100,000 exposed industrial control systems
Understanding GDPR Vendor Management and Compliance for your Business
General Data Protection Regulation (GDPR) is a framework for data protection that gives strict obligations for organizations within the European Union. For many businesses, understanding and implementing GDPR vendor management is a daunting task. That’s why we are going to break down what GDPR vendor management is, who is involved in it, and what the requirements are.