Netwrix Usercube: Identity Governance and Administration (IGA)
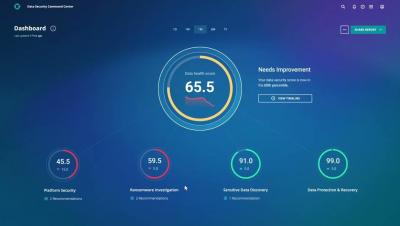
Learn why identity governance and administration (IGA) is the foundation of IT security, see real-world examples of effective IGA implementations and explore the benefits of choosing the right IGA solution.