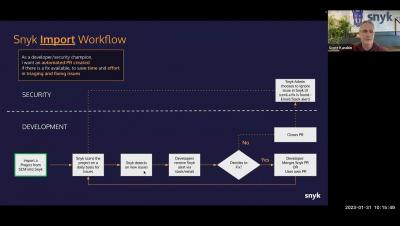
Snyk Workflows - Basic Workflows (IDE & CLI)
Snyk integrates with your IDEs, repos, workflows, and automation pipelines to add security expertise to your toolkit. The “menu” of options available to you is extensive, so we created this three-part series to get you started and running. The first session covers basic workflows in the IDE and CLI. You’ll learn to proactively plan how to leverage Snyk in different places and different ways. We will cover basic workflows and how to use them, as well as quick tips.