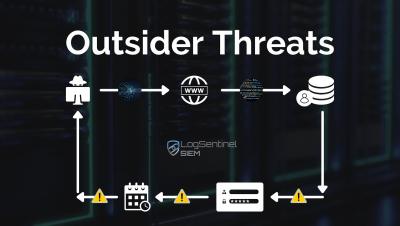
Case Study: Outsider Attacks - Before and After LogSentinel SIEM
Cyber attackers are relentless, but your security doesn’t have to be. Hackers can wreak havoc on your company. One way they do this is by attacking your IT infrastructure and look for vulnerabilities. The good news is, you don't have to spend a fortune to solve your security problems. LogSentinel SIEM is the first line of defense for organizations worldwide, helping businesses avoid security breaches before they happen.