Using the Voronoi - Data Search and Activeboards
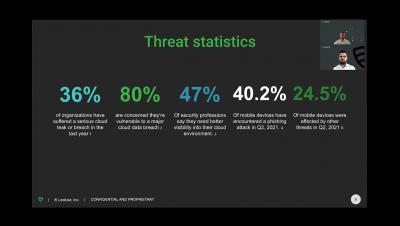
When graphically representing data to globally analyze the composition of a given data set, the Voronoi treemap is one of the most valuable tools. Discover everything that Devo offers you to create and use the Voronoi.