Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Compliance
Take it From a Compliance Officer: Secure Networks Matter
Even before the fiasco at Silicon Valley Bank, financial institutions were under tremendous scrutiny from regulators. How could they not be? Banks are among the oldest known targets for theft, and in a digital age, the best way to extract money is going to be either straight cyber-theft from existing accounts or ransomware. IT systems that house customers’ financial data can be architected with the right security controls in place to protect that data to the highest standard.
Our approach to threat modeling
In this series, you’ll hear directly from Vanta’s Security, Enterprise Engineering, and Privacy, Risk, & Compliance Teams to learn about the team’s approach to keeping Vanta — and most importantly, our customers — secure. The following post comes from our Security Team and explains our approach to threat modeling.
The key to 21 CFR Part 11 Compliance
21 CFR Part 11 is a set of regulations issued by the U.S. Food and Drug Administration (FDA) that establishes the criteria under which electronic records and signatures are considered trustworthy, reliable, and equivalent to paper records. In order to sell products in the United States, companies must demonstrate that their systems meet the standards set forth in Part 11. This can be a daunting task, as the requirements are numerous and detailed.
TrustCloud Launches TrustHQ for Atlassian, upgrading Jira to become the central hub for all GRC activities
What to do if your company suffers a data breach
Becoming aware that your company has suffered a data breach can be unsettling. However, due to the nature of cybercriminal activity, it is crucial to react quickly and correctly to contain the incident, minimize any further damages, and protect your business from legal troubles. Data breaches are affecting millions of people across the globe, with over 340 million records already compromised in 2023 headline cases and new incidents surfacing every week.
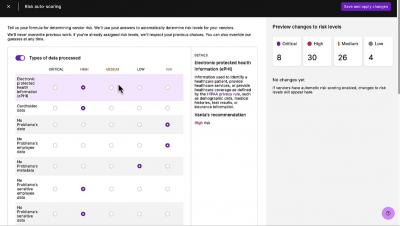
Improve your risk posture: Introducing Risk Management customization
Today we’re excited to announce Risk Management customization, a collection of new capabilities in our platform that enhance the existing Risk Management solution and give you more flexibility to enable custom risk management scoring and prioritization. Currently in beta, Risk Management customization will be generally available in the coming months.
Why Compliance Monitoring Is Critical for Your Business: Benefits and Best Practices
As regulatory requirements continue to evolve and data breaches become more common, businesses are under increasing pressure to maintain compliance with industry standards. Compliance monitoring is a crucial aspect of this process, enabling organizations to identify and address potential risks before they lead to costly violations or incidents.
The Role of Compliance in Mitigating Identity Theft Risks
In the digital age, identity theft poses a pervasive threat that organizations, regardless of their size or sector, must relentlessly combat. This insidious form of cybercrime involves the malicious exploitation of sensitive and confidential data, carrying grave implications for any organization. The consequences of a single breach can encompass financial losses, irreparable damage to reputation, and the imposition of regulatory penalties.