How Vanta combines automation & customization to supercharge your GRC program
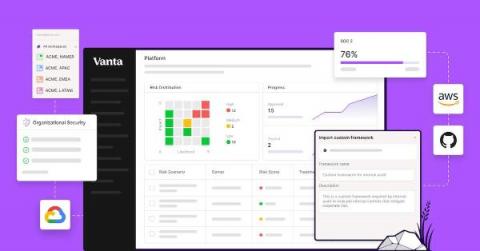
As the industry’s first automated compliance platform, Vanta includes a wealth of pre-built content, which enables customers without existing compliance processes to quickly get up and running. But more mature organizations may already have a compliance program — from the processes they follow to the definitions of their compliance and security surface area — that is built to meet their unique compliance goals, auditor requirements, and tech stack.