Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
API
Introducing Bearer inventory
The engineering organization of companies building modern cloud applications can get incredibly complex. Security teams are caught between the explosive growth of engineering teams and the fragmentation of software architecture. As a result, it can be a challenge to get a clear, complete and up-to-date view of engineering components. Bringing clarity about the software architecture is the first step to enable you to assess and remediate data security risks properly.
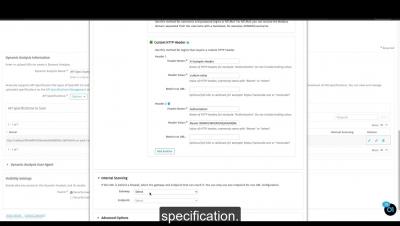
Create an API Specification Scan
How and why we built Masked Email with JMAP - an open API standard
Our core values as a company center around our users’ privacy, security, and satisfaction. While developing Masked Email – our integration with Fastmail that lets users create new, unique email addresses without ever leaving the sign-up page – we needed a technology that brought all three values together.
How adopting an OKR process has helped the Bearer team stay aligned
Keeping a team aligned isn’t easy. Not every meeting can possibly include every single team member, and updating a multitude of Notion pages with all the details regarding every discussion is an entire project in itself. The data that informs decisions is shared to separate groups of people, many of which don’t necessarily work closely together.
Credenxia leaps into the future with Dock's API
Kong Mesh and Styra DAS - securing modern cloud-native applications
Back at KubeCon North America 2017, many speakers declared that 2018 would be “The Year of the Service Mesh”. Just a year later, in the 2019 CNCF Survey1, it was reported that 18% of surveyed organizations were using a service mesh in production, and by 20202 (the most recent survey published at the time of this writing) that number rose to 27%.
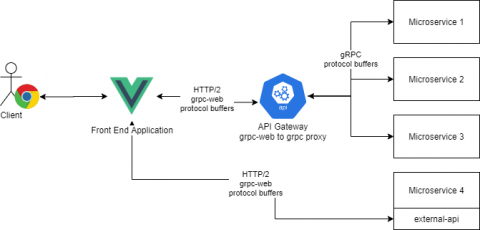
gRPC-web: Using gRPC in Your Front-End Application
At Torq, we use gRPC as our one and only synchronous communication protocol. Microservices communicate with each other using gRPC, our external API is exposed via gRPC and our frontend application (written using VueJS) uses the gRPC protocol to communicate with our backend services. One of the main strengths of gRPC is the community and the language support. Given some proto files, you can generate a server and a client for most programming languages.
Styra Declarative Authorization Service Expands Service Mesh Use Case
We are thrilled to announce native support of Kong Mesh, Istio and Kuma within Styra Declarative Authorization Service (DAS), enabling users to combine stellar service mesh solutions with the only authorization management platform that supports trusted cloud architecture. Styra DAS allows teams to manage policies across a broad spectrum of systems, like Kubernetes, microservices, public cloud, and more.