#CybersecuritySessions #onlinesafety #leadership
#botmanagement #cybersecurity #onlinesafety
#onlinesecurity #cybersecurity #defensiveai
#botmanagement #cybersecurity #automatedtraffic
#onlinesecurity #cybersecurity #onlinesafety
#cybersecurity #BLADEFramework #podcast
#Cybersecurity #podcast #onlinesecurity
- February 2025 (10)
- January 2025 (6)
- December 2024 (3)
- November 2024 (4)
- October 2024 (3)
- September 2024 (8)
- August 2024 (5)
- July 2024 (3)
- June 2024 (2)
- May 2024 (2)
- April 2024 (1)
- March 2024 (3)
- February 2024 (3)
- December 2023 (1)
- November 2023 (4)
- October 2023 (3)
- September 2023 (6)
- August 2023 (5)
- July 2023 (4)
- June 2023 (2)
- May 2023 (2)
- April 2023 (1)
- February 2023 (3)
- January 2023 (1)
- December 2022 (2)
- November 2022 (10)
- October 2022 (6)
- September 2022 (11)
- August 2022 (7)
- July 2022 (4)
- June 2022 (7)
- May 2022 (1)
- April 2022 (5)
- March 2022 (3)
- February 2022 (11)
- January 2022 (9)
- December 2021 (9)
- November 2021 (5)
- October 2021 (5)
- September 2021 (23)
- August 2021 (7)
- July 2021 (4)
- June 2021 (6)
- May 2021 (9)
- April 2021 (10)
- March 2021 (4)
- February 2021 (3)
- January 2021 (1)
- December 2020 (2)
- November 2020 (6)
- October 2020 (18)
- September 2020 (3)
- August 2020 (2)
- July 2020 (1)
- June 2020 (3)
- May 2020 (1)
- April 2020 (1)
- April 2019 (1)
- October 2018 (2)
- August 2018 (2)
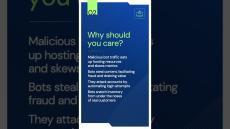
Netacea provides a revolutionary bot management solution that protects websites, mobile apps and APIs from malicious attacks such as scraping, credential stuffing and account takeover.
Our Intent Analytics™ engine, powered by machine learning, quickly and accurately distinguishes bots from humans to protect websites, mobile apps and APIs from automated threats while prioritising genuine users. Actionable intelligence with data-rich visualisations empowers you to make informed decisions about your traffic.
We Prevent Sophisticated Automated Threats:
- Account Takeover: Stop account takeover by identifying account-based attacks.
- Credential Stuffing: Prevent data breaches and protect your website from credential stuffing attacks.
- Fake Account Creation: Prevent fake account fraud by identifying bot accounts, fake account creation and mass account registration.
- Web Scraping: Identify and block web scrapers and scraping attacks made to compromise your website.
- Ad/Click Fraud: Identify ad fraud to reduce wasted spend and prevent ad bots from illegitimately displaying or accessing ads.
- Skewed Marketing Analytics: Prevent bots from stealing your marketing budget and skewing your analytics.
A Smarter Approach to Bot Management.