Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
November 2023
Wallarm to Unveil New API Security Solution and Strategic Shift at Black Hat Europe 2023
If you're involved with cybersecurity and are based in Europe, then Black Hat Europe 2023 in London, December 6 and 7 is a must-attend event. Wallarm, the experts in API and Application Security, will be attending the event, and we're excited to connect with you. If you are planning to attend, come by our booth or feel free to schedule a slot to meet with our API and App Security experts.
STEP Program with Bright Security: DAST Solutions and API Testing
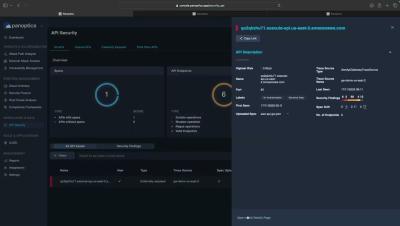
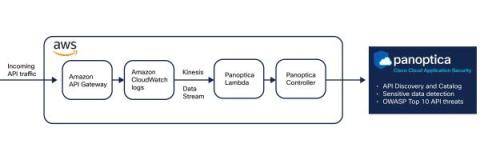
Panoptica API Security - Introducing AWS API Gateway Support
API Security Standards and Protocols: A Primer
Enhancing Developer Experience and Security Reporting on Workflows
In our previous blog post, we introduced Bearer’s new GitHub App and highlighted its seamless onboarding process and on-demand scanning capabilities. Today, we focus on how this app can significantly enhance the developer experience within Pull Requests (PRs) while providing critical reporting capabilities to security teams.
Unpacking the Zimbra Cross-Site Scripting Vulnerability (CVE-2023-37580)
On November 16, 2023, a significant security concern was published by Google's Threat Analysis Group (TAG). They revealed an alarming vulnerability in Zimbra Collaboration, a widely-used email hosting tool for organizations. This vulnerability, designated with an identifier, CVE-2023-37580, is a glaring example of a reflected cross-site scripting (XSS) issue. It allows malicious scripts to be injected into unsuspecting users' browsers through a deceptively simple method: clicking on a harmful link.
Secure incoming Amazon API Gateway traffic with Panoptica
Expanding LimaCharlie with API Integrations
Introducing Bearer's GitHub App
We are thrilled to introduce the Bearer GitHub App, a powerful addition designed to streamline your workflow and elevate your security practices.
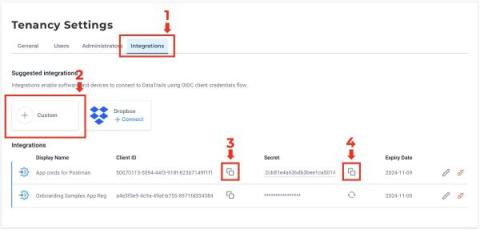
Postman Configuration for DataTrails
One of my favourite tools for playing with REST APIs is, of course, Postman. It can make interacting with DataTrails super quick and easy, and help you develop custom workflows for storing and validating your digital provenance and audit trails. Here’s a step-by-step guide to getting a robust Postman set-up configured, and if you head over the Postman public collections you’ll find a link to a pre-baked DataTrails Postman collection with this done for you, along with some example requests.
Securing Your Web Applications and APIs with Dynamic Analysis
Web applications are one of the most common vector for breaches, accounting for over 40% of breaches according to Verizon's 2022 Data Breach Report. Ensuring that your web applications are sufficiently protected and continue to be monitored once they are in production is vital to the security of your customers and your organization.
Improper Authorization in Confluence Data Center and Server (CVE-2023-22518)
In early November, the cybersecurity community witnessed the exploitation of a zero-day vulnerability in Confluence Data Center and Server. This critical vulnerability was related to Improper Authorization and assigned CVE-2023-22518 identifier. In this blog, we delve into the details of these vulnerabilities, their implications, and the necessary mitigation steps to protect your digital assets.
Handle secrets like API keys securely in javascript projects with environment variables
Navigating Threats - Insights from the Wallarm API ThreatStats Report Q3'2023
The world of digital technology is perpetually evolving, positioning cybersecurity as a frontline defense in safeguarding essential digital assets. A primary challenge in this sector, accentuated by the Wallarm API ThreatStats™ report Q3’2023, is ensuring robust API security. This in-depth report emphasizes the urgent need for immediate, strategic actions from business leaders and cybersecurity practitioners alike to combat the sophisticated emerging threats.
Securing APIs: Practical Steps to Protecting Your Software
In the dynamic world of software development, Application Programming Interfaces (APIs) serve as essential conduits, facilitating seamless interaction between software components. This intermediary interface not only streamlines development but also empowers software teams to reuse code. However, the increasing prevalence of APIs in modern business comes with security challenges.
Testing with OpenAPI Specifications
The 2023 SANS Survey on API Security (Jun-2023) found that less than 50 percent of respondents have API security testing tools in place. Even fewer (29 percent) have API discovery tools. Wallarm delivers both these capabilities via our single, integrated App and API Security platform. Wallarm has long offered the ability to generate OpenAPI Specifications (aka Swagger) based on actual traffic across your endpoints.