Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Zero Trust
Healthfirst Applies An Identity Security First Approach To Implement Zero Trust | CyberArk
Keeper Connection Manager Adds New, Next-Gen Features for Zero-Trust Network Access
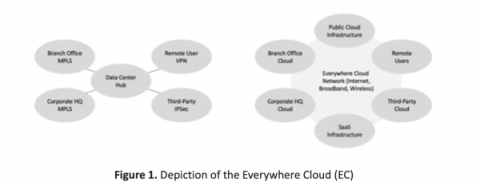
Corelight for the everywhere cloud
Editor's note: This is the first in five-part series authored by Ed Amoroso, founder and CEO of TAG Cyber, which will focuses on how the Corelight platform reduces network security risks to the so-called Everywhere Cloud (EC). Such security protection addresses threats to devices and assets on any type of network, including both perimeter and zero-trust based.
Does Your Organization Meet the 9 Core Capabilities Essential for Zero Trust in IoT?
Every one of your IoT devices has their own machine identity. But how are these identities the key to achieving Zero Trust IoT project? Today’s PKI (Public Key Infrastructure) vendors have specific solutions for managing non-human identities – machines – like servers, laptops, software applications, API’s and other assets found within a corporate network.
Understanding the basics of Cloud Security: What is Zero Trust & Why does it Matter?
Cybersecurity professionals are tasked with the difficult job of protecting their organization's data from malicious actors. To achieve this goal, zero trust security has become an essential tool for organizations. But what exactly is zero trust? In this post, we’re going to separate signal and noise by disambiguating the term zero trust. We’ll talk about what it is, why it matters, and key takeaways you should have regarding the state of cybersecurity in 2023.
Myth Busting: Why Moving From VPN to ZTNA Doesn't Have to be a Heavy Lift
Over the last few years many organizations have already introduced a zero trust network access (ZTNA) solution, and are seeing the benefits from it. But many others have been put off by the work needed to transition to a zero trust-based access model and the associated technical integration work.