Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Multi-Factor is incomplete without backup codes
I was logging into one of my favorite online shopping sites the other day, and, as with all my other sites, I was presented with the multi-factor authentication prompt to complete the login process. Anyone who knows me, knows that I have been a long-time supporter of multi-factor, or 2-step verification of any kind.
How 1Password keeps your account data safe from cyber attacks
Several layers of protection guard the data you store in 1Password, but is it enough to defend against cyberattacks like credential stuffing?
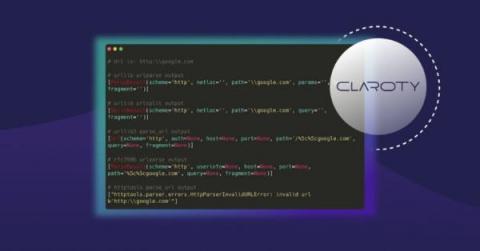
URL confusion vulnerabilities in the wild: Exploring parser inconsistencies
URLs have forever changed the way we interact with computers. Conceptualized in 1992 and defined in 1994, the Uniform Resource Locator (URL) continues to be a critical component of the internet, allowing people to navigate the web via descriptive, human-understandable addresses. But with the need for human readability came the need for breaking them into machine-usable components; this is handled with URL parsers.
Hello CISO - Episode 1 (Part 2): The Downfall of On-Premise Security
What is a Distributed Cloud Architecture? Top 4 Security Considerations
By 2025, there will be more than 100 zettabytes of data stored in the cloud – that’s a lot of data! With more applications needing to process a significant amount of data in real-time, there is a shift in demand for distributed cloud and edge computing. Fortunately, the distributed cloud brings many impressive benefits to organizations – generating immense cost savings, greater scalability, and reaching resource-intensive business demands.
What SecOps Teams Can Expect in 2022
Traditionally, most organizations have had siloed departments wherein teams’ activities are highly separated and the objectives within organizational structures are divided. This operational methodology has brought about friction – especially within the IT department, where developers and ITOps lack collaboration.
Offline Access on a Mobile Device
Where is Low-Code Going in 2022? 8 Hot Trends and Predictions (Part 1)
What’s the trick to staying competitive in 2022? The ability to quickly adjust your business models and processes. You need only rewind to 2020 to see why. A worldwide pandemic. The need to create new business models, innovate new business processes, establish new means of interacting with customers… with little warning and small budgets. And all this just to stay afloat. For many of the businesses that succeeded, low-code development solutions were part of their success.