How Calico Network Threat Detection Works
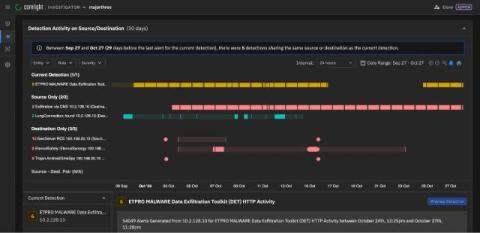
In today’s cloud-native environments, network security is more complex than ever, with Kubernetes and containerized workloads introducing unique challenges. Traditional tools struggle to monitor and secure these dynamic, interconnected systems, leaving organizations vulnerable to advanced threats, such as lateral movement, zero-day exploits, ransomware, data exfiltration, and more.